Attack Surface Management
Stay ahead of cybercriminals and your rapidly expanding attack surface through comprehensive visibility of your digital infrastructure. Attack Surface Management helps you inventory your assets, identify and eliminate vulnerabilities, and secure your networks.
Increased visibility of your attack surface through a comprehensive security process
An Attack Surface Management solution should give you:
- A complete inventory of your network, server, and cloud assets for increased visibility of your overall threat surface.
- A detailed attack surface map, demonstrating where cybercriminals may penetrate and move through your network.
- A comprehensive view of security exposures, potential attack paths, and their resulting blast radius.
- A specific view of all the internet-facing assets in your organization — which are most vulnerable to attack.
All cybersecurity starts with greater visibility of your attack surface
In today’s technically complex world, organizations often struggle to see the full picture of their IT landscape. This becomes increasingly challenging when you add in distributed...
In today’s technically complex world, organizations often struggle to see the full picture of their IT landscape. This becomes increasingly challenging when you add in distributed IT ecosystems, have data locked in silos or have teams all over the globe. Only a good map and inventory of your attack surface makes it straightforward to know where your most critical exposures lie.
There are a lot of security solutions on the market – each serving their own siloed purpose. As standalone solutions, they leave gaps and are not...
There are a lot of security solutions on the market – each serving their own siloed purpose. As standalone solutions, they leave gaps and are not enough to keep you protected. With the lack of visibility, business context, and automation, security teams are constantly burdened by long task lists, with little end or clarity in sight.
The number of vulnerabilities continues to grow every year. In 2022 alone, there were 25k new vulnerabilities (see Vulnerability and Threat Trends Report 2023) which...
The number of vulnerabilities continues to grow every year. In 2022 alone, there were 25k new vulnerabilities (see Vulnerability and Threat Trends Report 2023) which means you’re being overwhelmed with many thousands of critical or high vulnerability alerts, without any understanding of which represent the most risk to the organization.
The value of Attack Surface Management
Attack Surface Management (ASM) is vital for modern organizations due to the rapid evolution of technology and the expanding complexity of digital environments. ASM not only helps to improve your overall security posture, but also allows you maximize the impact of your existing security investments while your team’s time is focused to reduce the most risk.
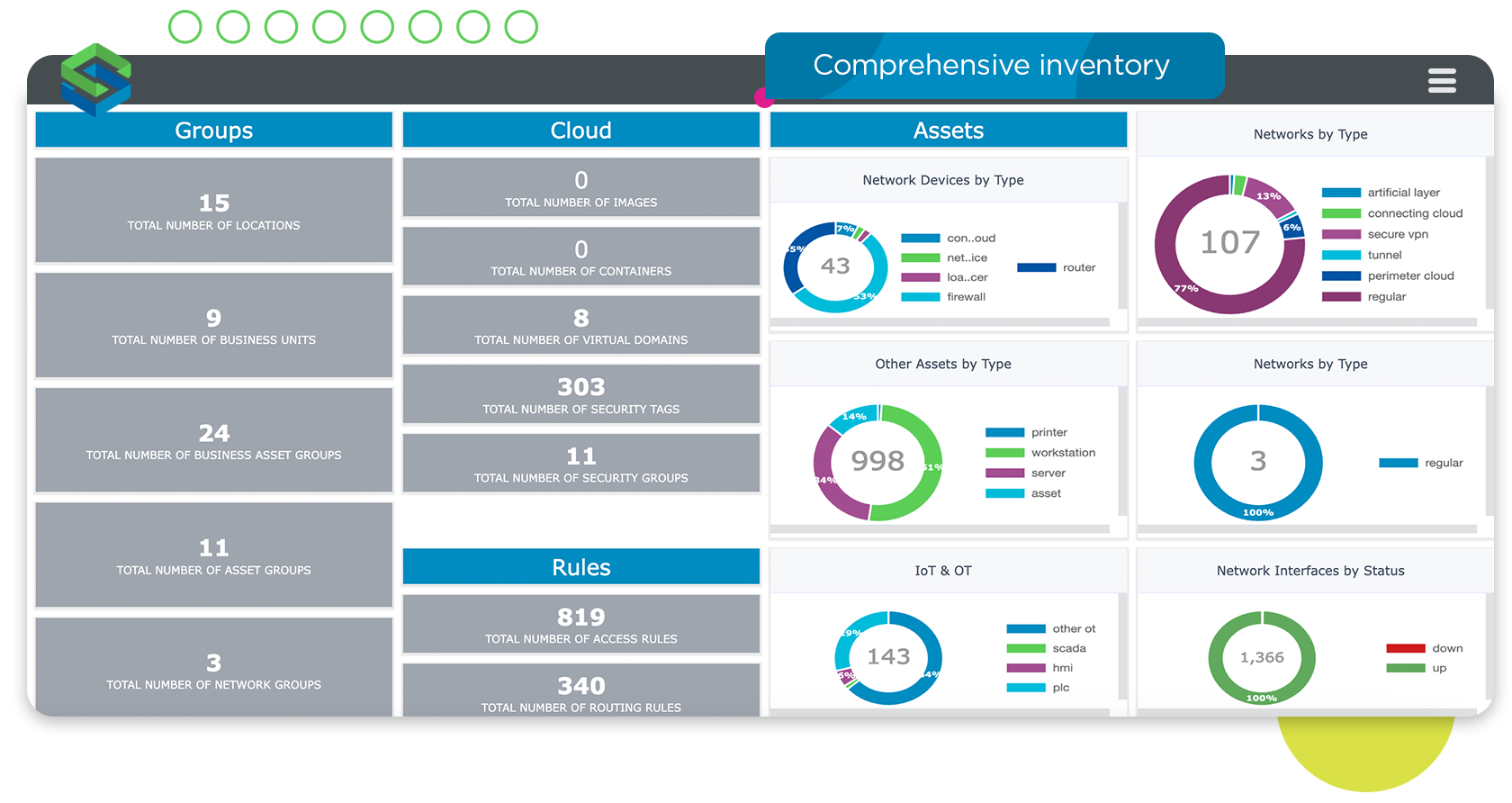
Attack Surface Management allows you to automatically and continuously discover all attackable assets in your enterprise, including devices on-premises or in the cloud, OT and IT assets.
Inventory attackable assets to see where vulnerabilities lie
The key to protecting your critical assets is knowing where – and how – they are vulnerable to cybercriminals. Attack Surface Management allows you to continuously discover and inventory all attackable assets in your enterprise, including networks, servers, cloud resources, and OT assets. Improved asset visibility strengthens cybersecurity, ensures compliance, and enhances the organization’s ability to respond to incidents and recover from them.
A good Attack Surface Management solution will provide a comprehensive inventory of:
Digital assets including network devices, servers, cloud services, and OT devices
Firewall security policy and network access information
Business-related details such as location, ownership, and importance
Detailed metadata about each asset
Unmatched Visibility with Cyber Asset Attack Surface Management (CAASM)
Cyber Asset Attack Surface Management (CAASM) is one of the key pillars of Attack Surface Management. It allows you to record information about every attackable asset in the estate including devices, networks, applications, and users to give you a “birds-eye view” of your exposure.
Map the attack surface for improved visibility of threats
Using the asset inventory, your ASM solution builds a map of the attack surface, combining asset information with network topology, device infrastructure data, security and threat intelligence. This map helps you fully visualize your networks, including assets that can’t have an agent, such as OT or airgapped networks. With a clear view of how different assets interact through the network, you are more effective at security planning and incident response.
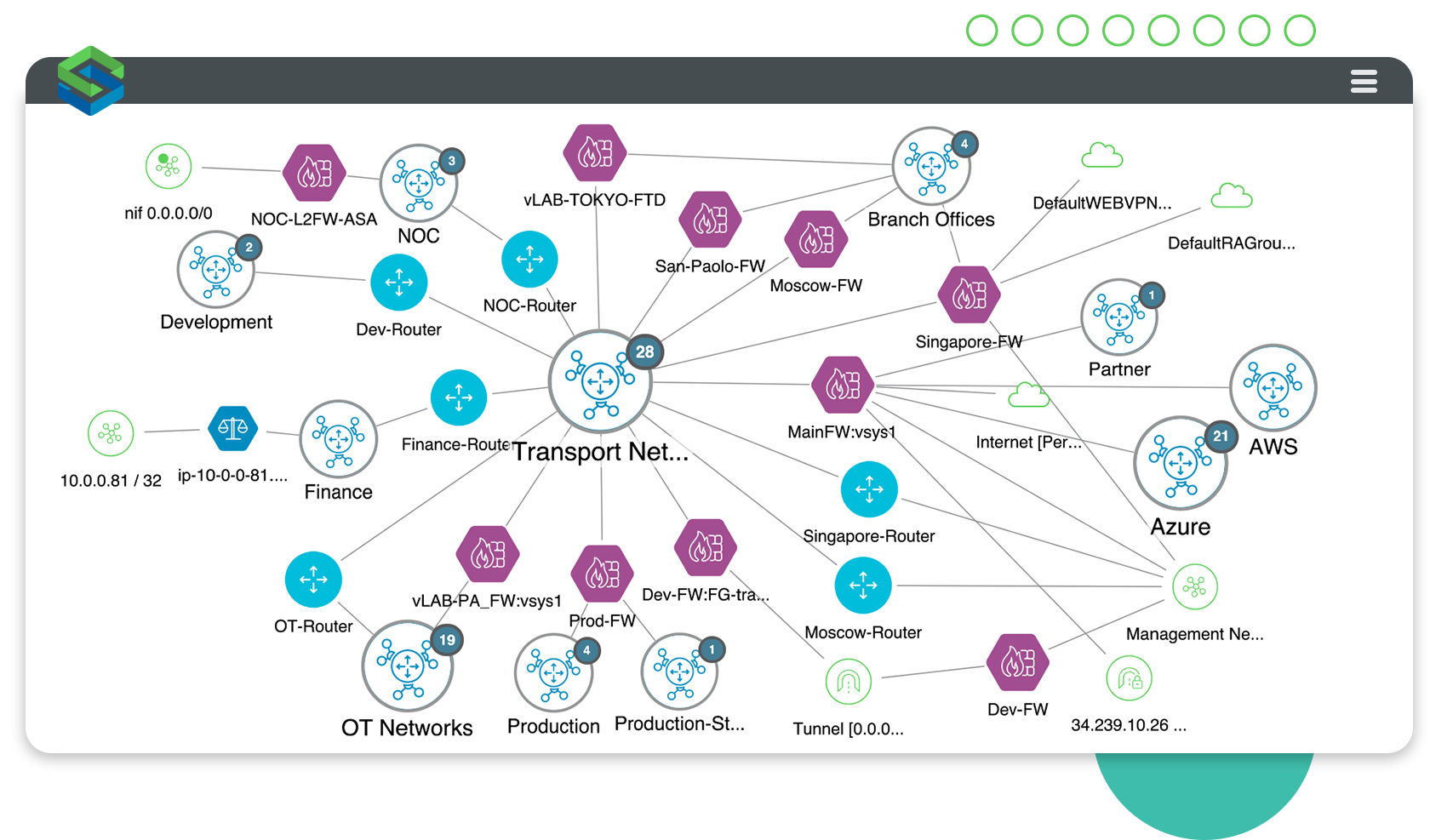
Build a map of your attack surface, combining asset information with network topology, infrastructure data, security, and threat intelligence.
Armed with knowledge of the network infrastructure, you can use the map to:
Drill down and examine individual networks or specific business units.
Respond quickly to emerging threats and ongoing attacks.
Understand where security controls or monitoring tools should be placed.
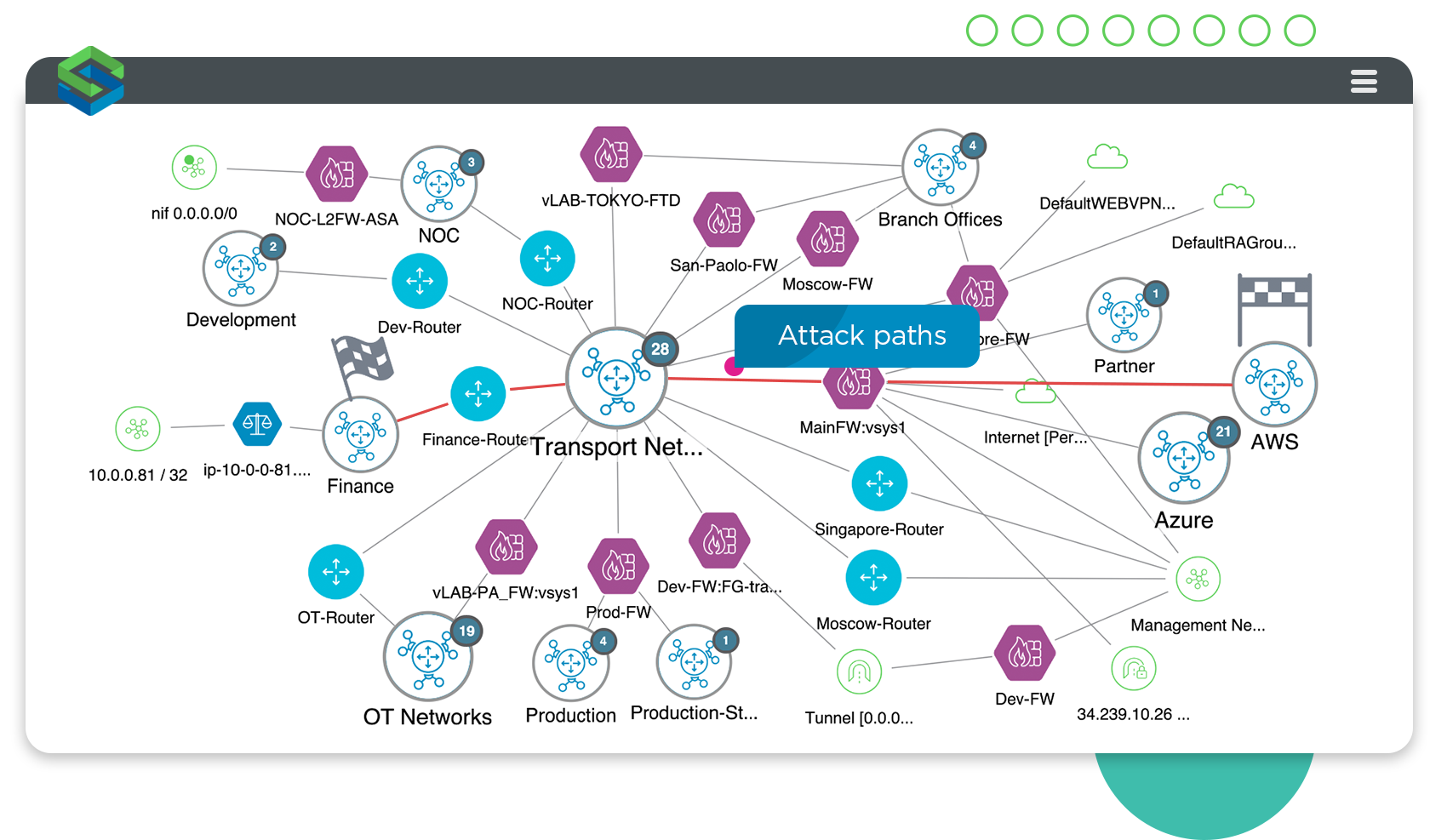
Visualize end-to-end attack paths, understand lateral movement and blast radii, and simulate attacks.
Reveal potential attack paths for quicker time to remediation.
With a comprehensive attack surface map, you can view the hybrid attack surface, analyze exposure, and prioritize remediations based on what’s most important to your business. This helps you focus on your highest priorities and more quickly remediate the vulnerabilities that could cause the most damage to your environment.
A visualization of end-to-end attack paths equip you to understand the potential routes for attackers. Attack simulation shows exactly how a cybercriminal would be able to exploit a vulnerable asset, step-by-step across the network – right down to the individual device(s), configurations, and rules that would enable the attack – so you can take steps to prevent or block it. Lateral movement visualization illuminates the downstream exposure, and potential blast radius, from a compromise coming from lateral attacks, supply chain partners, and even insider threats.
Pinpoint Vulnerable Internet-Facing Assets with External Attack Surface Management (EASM)
External Attack Surface Management (EASM) is another key component of Attack Surface Management. It focuses on identifying and securing an organization’s digital assets that are exposed to the internet, such as websites, servers, cloud services, and internet-connected devices. EASM is crucial for protecting an organization’s public-facing infrastructure from evolving security threats.
Uncover your external threats to protect all entry points
Some of your greatest risks lie beyond your view, from assets that are openly exposed to the internet. A good Attack Surface Management solution gives you the ability to detect, inventory, and continuously monitor all the internet-facing assets in your organization — and pinpoint those which are most vulnerable to attack.
By identifying and prioritizing all the existing vulnerabilities in the organization that belong to internet-facing devices, you are prepared to secure those assets and protect your organization. This information, combined with attack surface visualization, means you see your network from an attacker’s point of view to better mitigate potential risks that might otherwise be overlooked or de-prioritized.
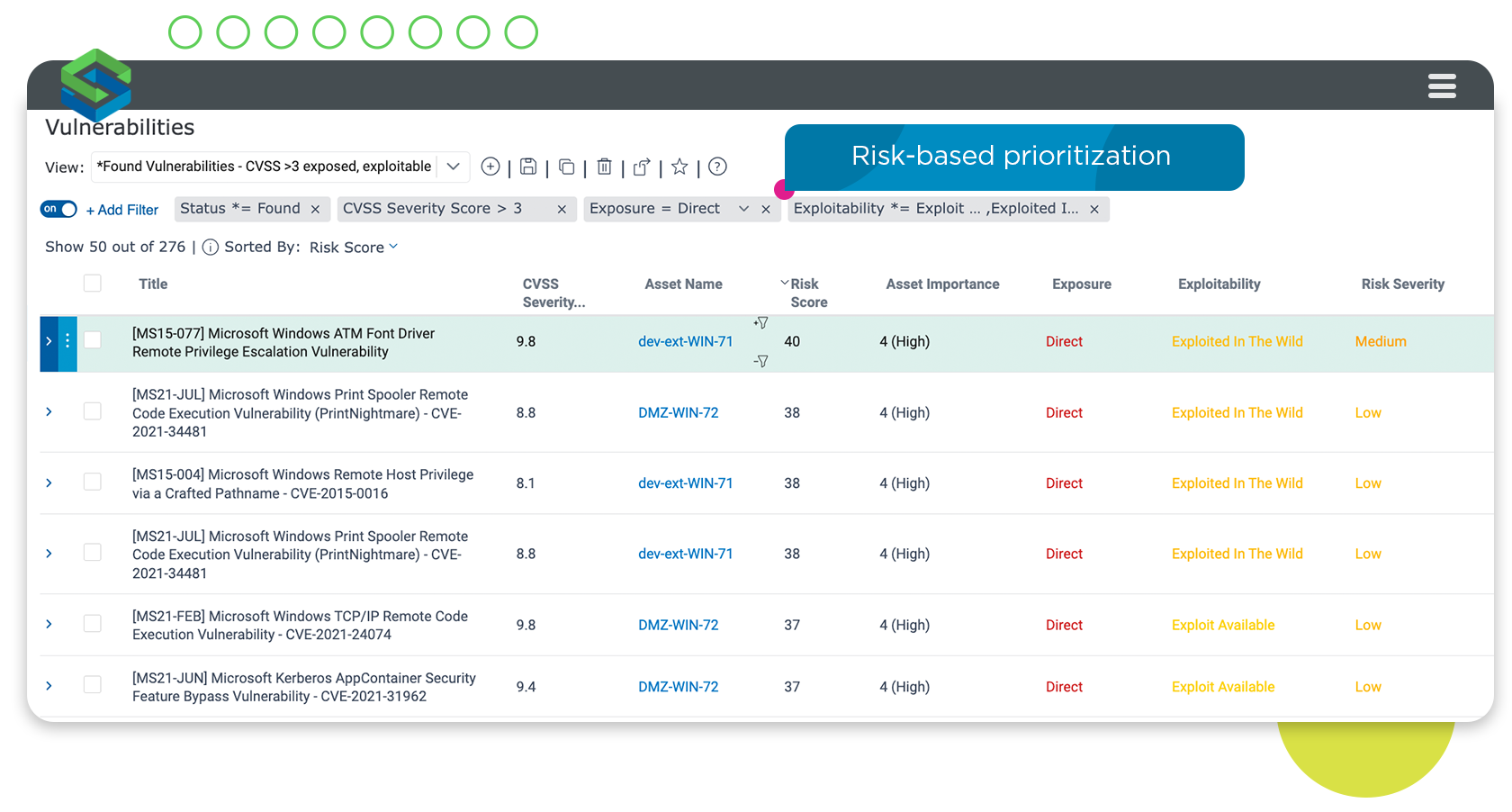
Detect and continuously monitor all your organization’s internet-facing assets to pinpoint those most likely to be vulnerable to an attack.
Related Skybox Products
These Skybox products include the Attack Surface Management capabilities required to visualize, analyze, and protect your most valuable and vulnerable assets from cyber threats.

Attack Surface Management allows you to automatically and continuously discover all attackable assets in your enterprise, including devices on-premises or in the cloud, OT and IT assets.

Build a map of your attack surface, combining asset information with network topology, infrastructure data, security, and threat intelligence.

Visualize end-to-end attack paths, understand lateral movement and blast radii, and simulate attacks.

Detect and continuously monitor all your organization’s internet-facing assets to pinpoint those most likely to be vulnerable to an attack.


