Skybox Products
Continuously manage your cyber exposure. Skybox exposure management products deliver proactive risk reduction across the hybrid attack surface.
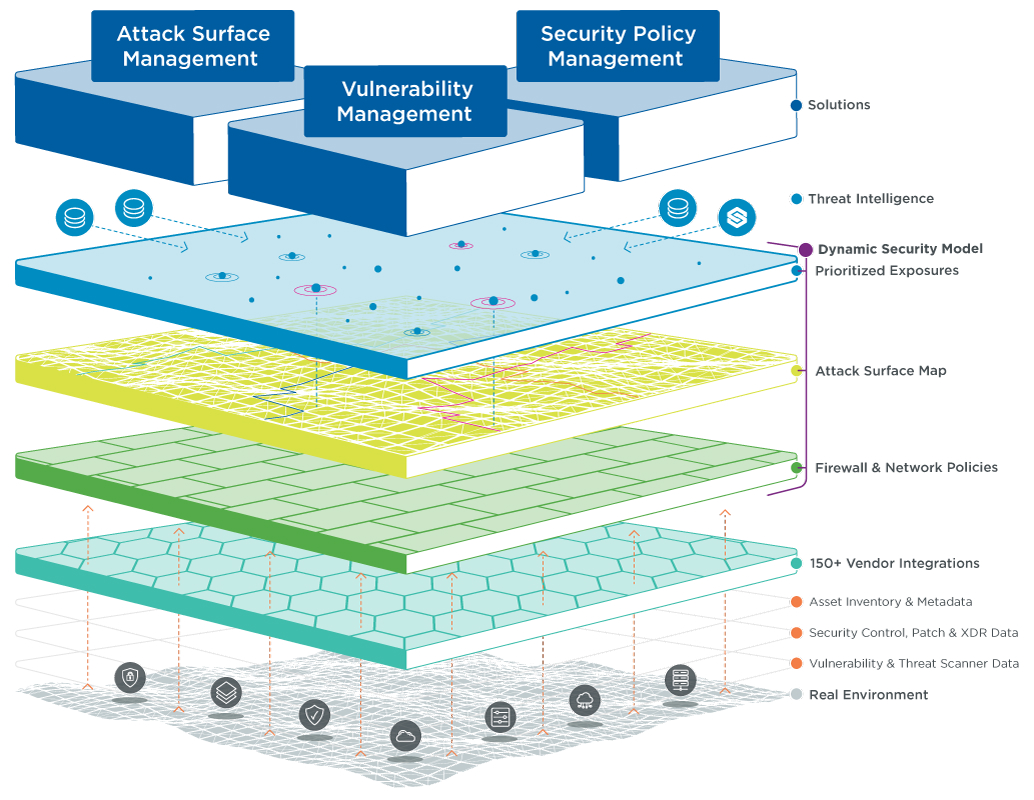
Skybox Continuous Exposure Management Platform
Continuously assess, prioritize, and remediate the cyber threats that matter most across your hybrid attack surface.
The Skybox platform supports each stage of your enterprise’s continuous exposure management program to map the attack surface and contextualize with data, assess and prioritize vulnerabilities, and combat the threat through final remediation. Integrated attack surface management, vulnerability management, and security policy management solutions make it easy to manage exposures and maximize the effectiveness of your security team.
Product capabilities
The Skybox platform is powered by a range of advanced platform, product, and deployment capabilities that work together to deliver comprehensive exposure management. With seamless integration into your existing systems, you reduce your exposure to risk and stay ahead of potential threats.

Skybox integrations
Skybox integrates with, and aggregates data from, leading network platforms, asset databases, and security technologies. Our integrations give you visibility across your digital ecosystem. This visibility is crucial to identify exposures as you understand the relationships between key data sources, the network, and your security model.