Vulnerability and Threat Management
In today’s complex technical world, most organizations are overwhelmed by many thousands of vulnerabilities in their environment — too many to find and patch in a timely manner. By implementing a comprehensive Vulnerability and Threat Management program, you maximize the value of the data from your security solutions to overcome the noise and prioritize efforts on the risks that truly matter to your organization.
Discover which vulnerabilities represent the highest risk to your organization
With a Vulnerability and Threat Management (VTM) solution, you can:
- Assess your attack surface.
- Discover potential attack paths.
- Prioritize which vulnerabilities are the highest risk.
- Remediate the most critical vulnerabilities.
- Report back risk and status to stakeholders.
Reduced risk with a modern vulnerability management approach
As the number of vulnerabilities grows, most IT have become inundated by the sheer volume of critical alerts. You need to prioritize based on the highest...
As the number of vulnerabilities grows, most IT have become inundated by the sheer volume of critical alerts. You need to prioritize based on the highest risk to know where to start and what remediations will most significantly impact your organization's security.
While it may seem simple enough to protect the assets you can see, how do you secure assets that can’t be scanned, like OT devices or...
While it may seem simple enough to protect the assets you can see, how do you secure assets that can’t be scanned, like OT devices or air-gapped networks? Without a scanner linked to these devices, it’s hard to know when one of them is at risk – and putting your critical assets in danger.
Most IT and security teams acknowledge timely patching is critical to securing vulnerable entrances. But patching windows are often far and few between, so what happens...
Most IT and security teams acknowledge timely patching is critical to securing vulnerable entrances. But patching windows are often far and few between, so what happens when you find a vulnerability that may take months to schedule before a patch can be applied? Finding compensating controls to mitigate the risk between patching windows is critical to reducing exposure.
Build out a modern vulnerability and threat management program
For many organizations, having a vulnerability scanner is a no-brainer – it’s essential to discovering vulnerabilities and is often part of your compliance requirements. But to better defend against cybercriminals, you need a modern approach to Vulnerability and Threat Management (VTM).
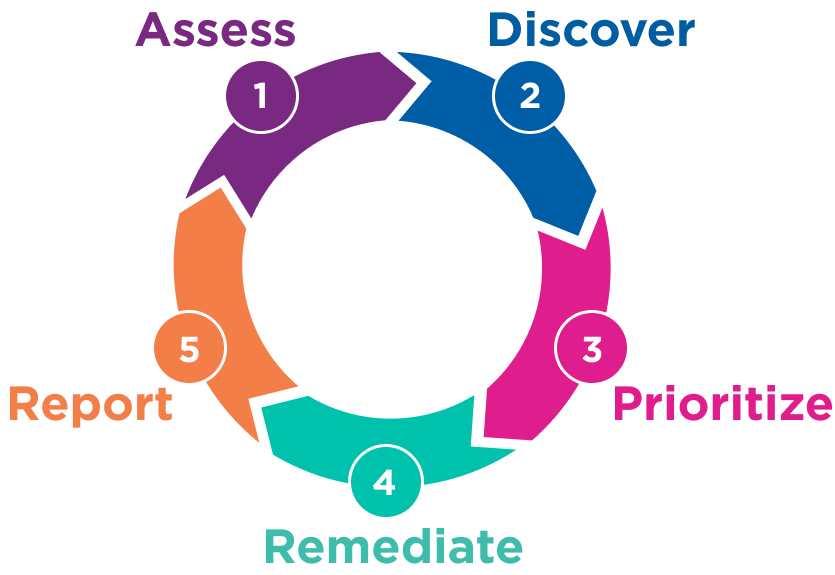
The five stages of a vulnerability and threat management program.
Assess your attack surface to stay better protected
With every passing year, the number of vulnerabilities in the wild rises. In 2022 alone, there were 25k new vulnerabilities, leaving teams overwhelmed with thousands of critical or high vulnerability alerts without understanding which represents the most risk to the organization. To truly understand – and mitigate – your risk, you must first understand your entire attack surface.
A good threat and vulnerability management solution should give you a unified view of your network by combining and aggregating data from multiple sources, such as network, server, and cloud infrastructure, for increased visibility of your overall threat surface.
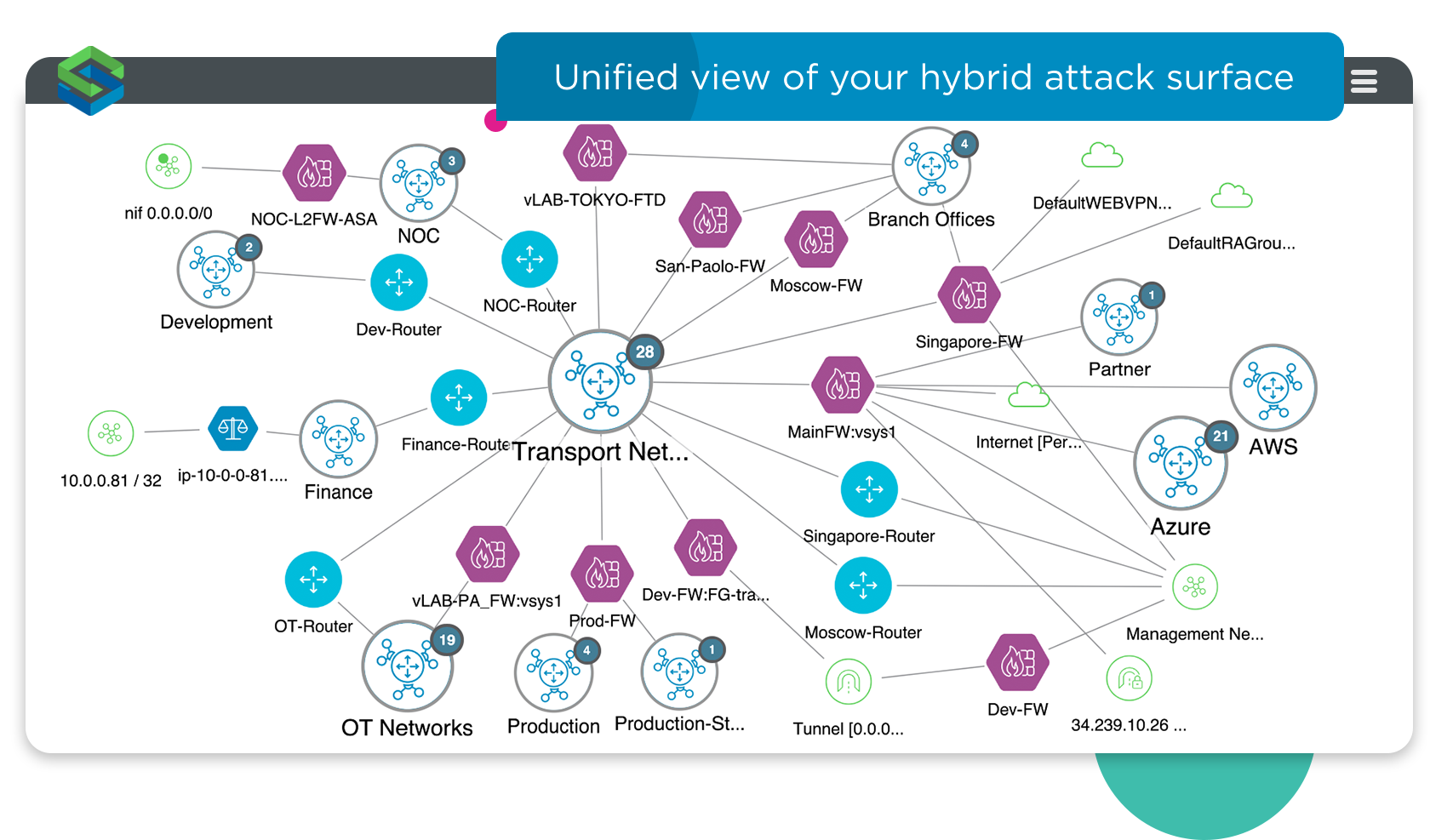
Build a map of your attack surface, combining asset information with network topology, infrastructure data, security, and threat intelligence.
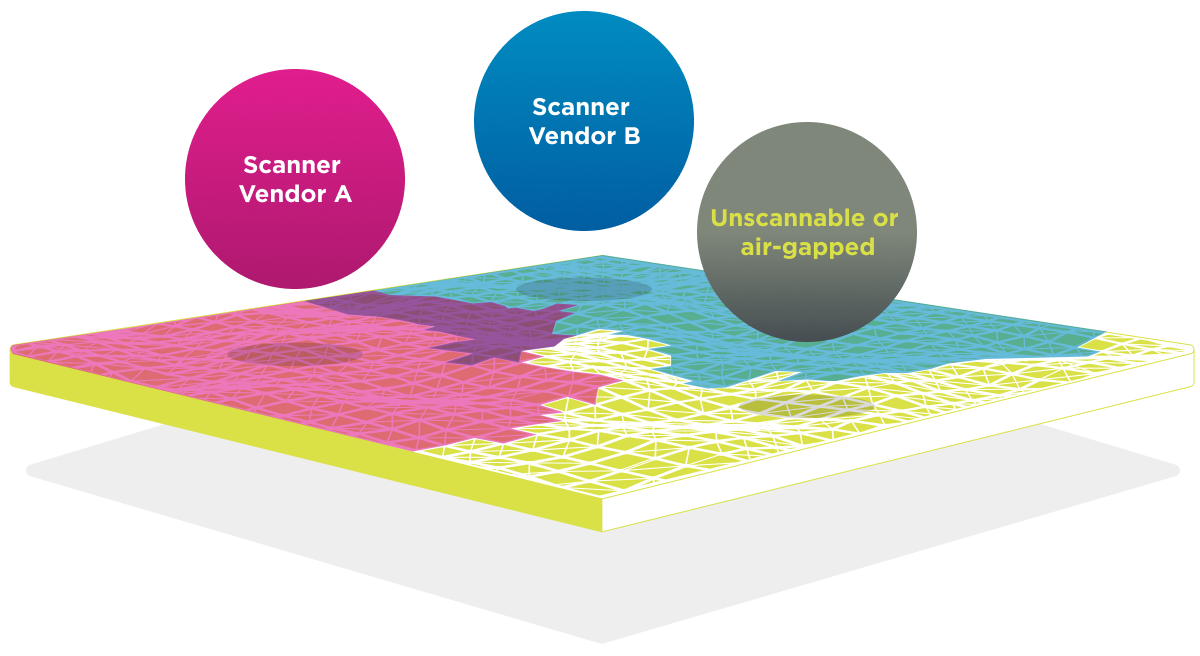
Understand your highest risks through comprehensive visibility of your networks
Discover vulnerabilities for a unified view of risk
Vulnerability scanners have long been an essential security tool; they provide awareness of the vulnerabilities in your environment, drive patching cycles, and help you stay compliant. However, data from a particular scanner only shows part of the picture. A risk-based vulnerability management solution provides additional visibility, including data from unscannable assets or air-gapped networks, to help you better understand your highest risks.
An effective VTM solution de-duplicates and aggregates data from multiple sources and combines it with the latest threat intelligence for a complete picture of your attack surface. The solution highlights exposures between the scheduled scan cycles – the “scanning awareness gap” – and drastically reduces risk and the likelihood of a breach.
Prioritize highest-risk threats to your organization
For most organizations, the large volume of threats in their environment is overwhelming. Many security teams focus on the CVSS score, specifically what’s labeled Critical or High, but this can be upwards of 50% of your total vulnerabilities. For a clearer picture of the highest risk exposures to your specific environment, you need a more sophisticated approach to prioritization of vulnerabilities. Understanding attack paths and dependencies across critical assets will provide you with a better understanding of your risks and allow your team to maximize their efforts and tackle the vulnerabilities that are most likely to hurt your business.
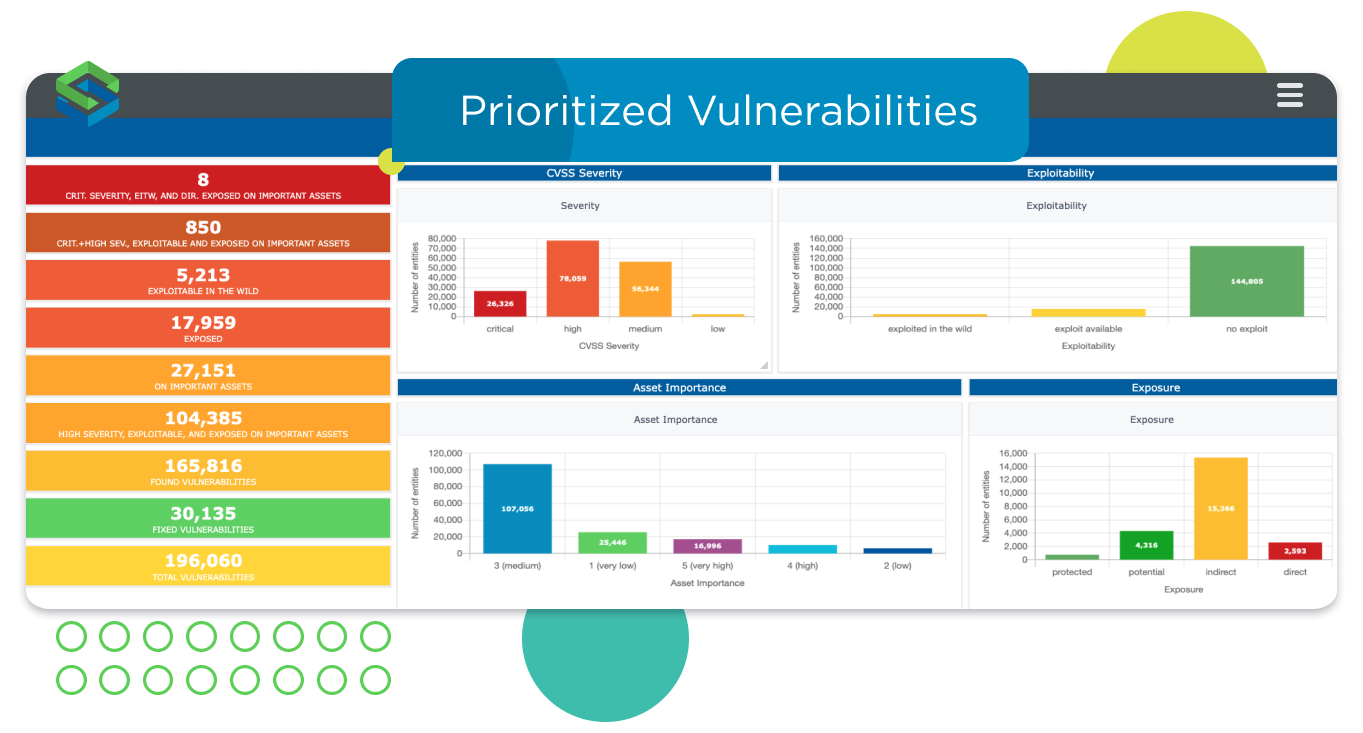
Understand what vulnerabilities pose the biggest risk to your organization
A risk-based vulnerability management solution should prioritize risk with factors such as:
CVE severity, as identified by the CVSS score
Business context, such as geography, technology, business function, applications, services, and owners
Exploitability in the wild, as in whether a threat actor is actively using a specific vulnerability
Accessibility of the asset, how easily an attacker can reach it from a threat origin, like the internet
Remediate and reduce risk with compensating controls
Patching vulnerabilities has historically been how IT teams have kept their devices secure. But patch cycles can disrupt business for many organizations, so they only run once a month, if not less often. A modern vulnerability management solution will not only shorten your scanning awareness gap, but also provide compensating controls to mitigate the risk of leaving a vulnerability unpatched until the next patch window — we call this window “patch lag”. This reduces your overall exposure significantly.
A modern VTM solution will prescribe and validate a series of compensating controls to lessen risk during this patch lag. These controls may include:
- An IPS signature
- Software updates
- Configuration changes
- Network segmentation
- Firewall rule modification
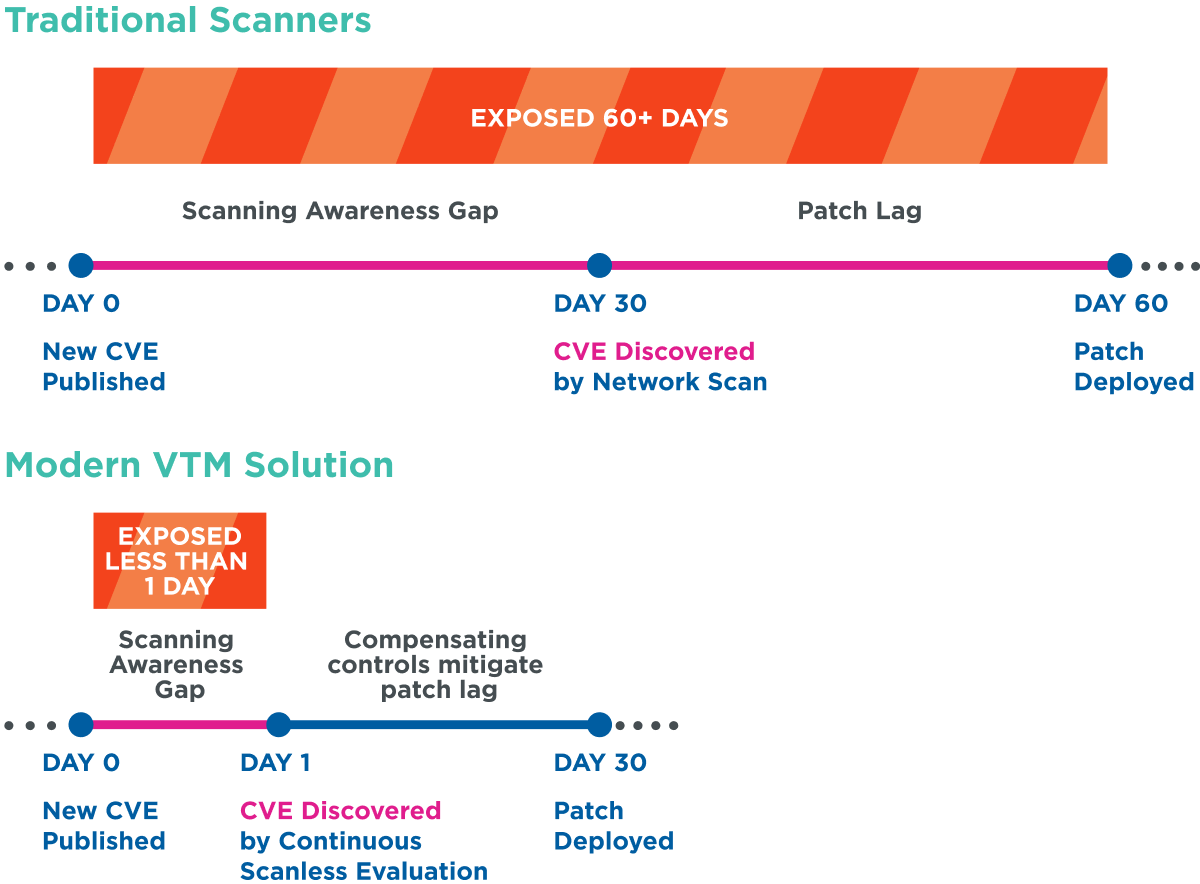
Reduce exposure from more than 60 days, to less than one with a modern VTM solution
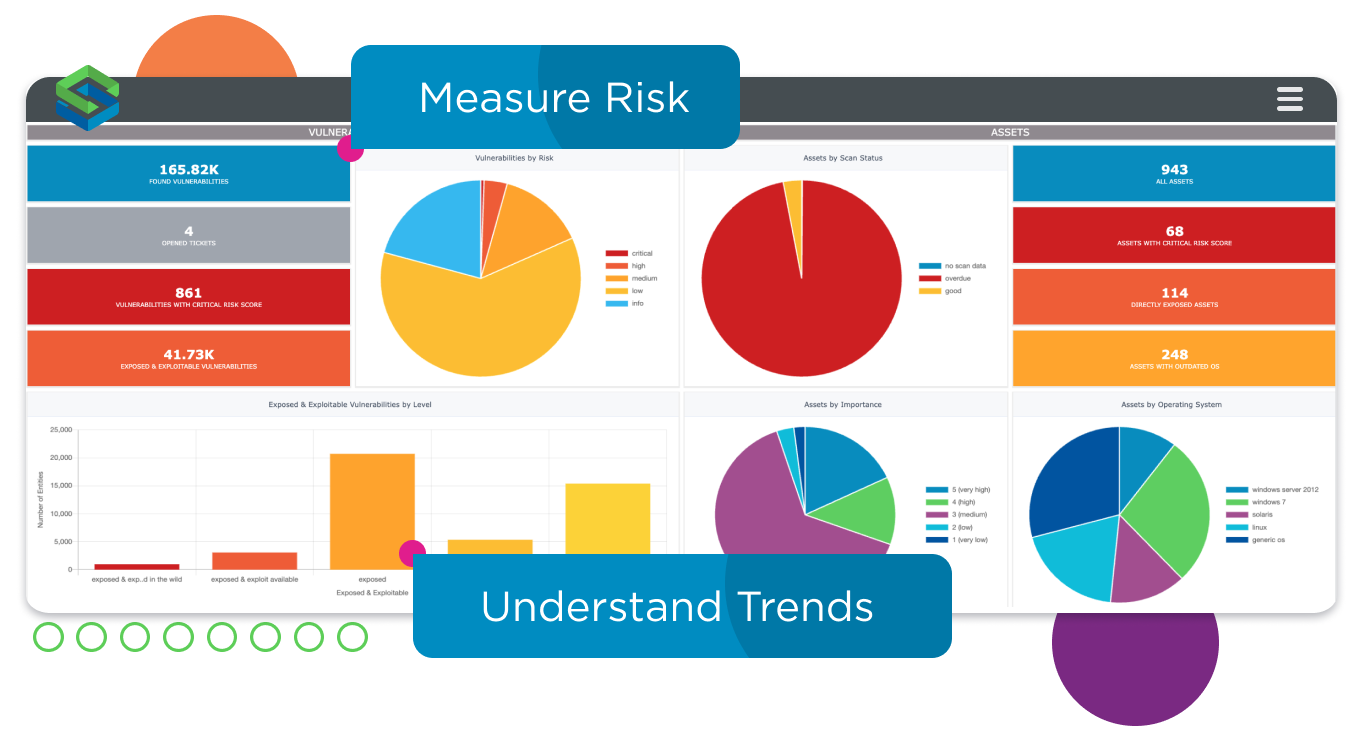
Focus your efforts on the vulnerabilities most likely to cause damage to your organization
Report to key shareholders for greater organizational visibility
For many companies, security is a team working hard in the background but not getting much attention – unless a bad actor breaches their network. However, security teams need to be able to demonstrate their work, specifically how they reduce exposure and risk for the organization.
A modern VTM solution gives you reports on trends and progress, such as the number of vulnerabilities remediated over time, as well as meeting SLA measurements. They provide a detailed risk analysis, vulnerability ticketing status, and help demonstrate and validate that you’re meeting compliance requirements. The reports should demonstrate your hard work and deliver valuable insights to inform decision-making and allow the team to assess overall cyber exposure.
Related Skybox Products
The Skybox VTM solution includes the product modules that help you see where your exposures lie, quantify the potential for exploitation, prioritize vulnerabilities that are most critical to your organization, and provide mitigation and remediation options to reduce risk.

Build a map of your attack surface, combining asset information with network topology, infrastructure data, security, and threat intelligence.

Understand your highest risks through comprehensive visibility of your networks

Understand what vulnerabilities pose the biggest risk to your organization

Reduce exposure from more than 60 days, to less than one with a modern VTM solution

Focus your efforts on the vulnerabilities most likely to cause damage to your organization