The specter of another SolarWinds maintains a constant consideration across the industry. The truth is that the likelihood of another global, mass cybersecurity event only increases as time goes on. We know that threat actors are working hard to make this happen. Skybox Security’s latest research, the Vulnerability and Threat Trends Report, revealed that the creation of new malware samples nearly doubled over 2020 as attackers sought to take advantage of pandemic-related disruption.
The business of cybercrime: malware-as-a-service gains pace
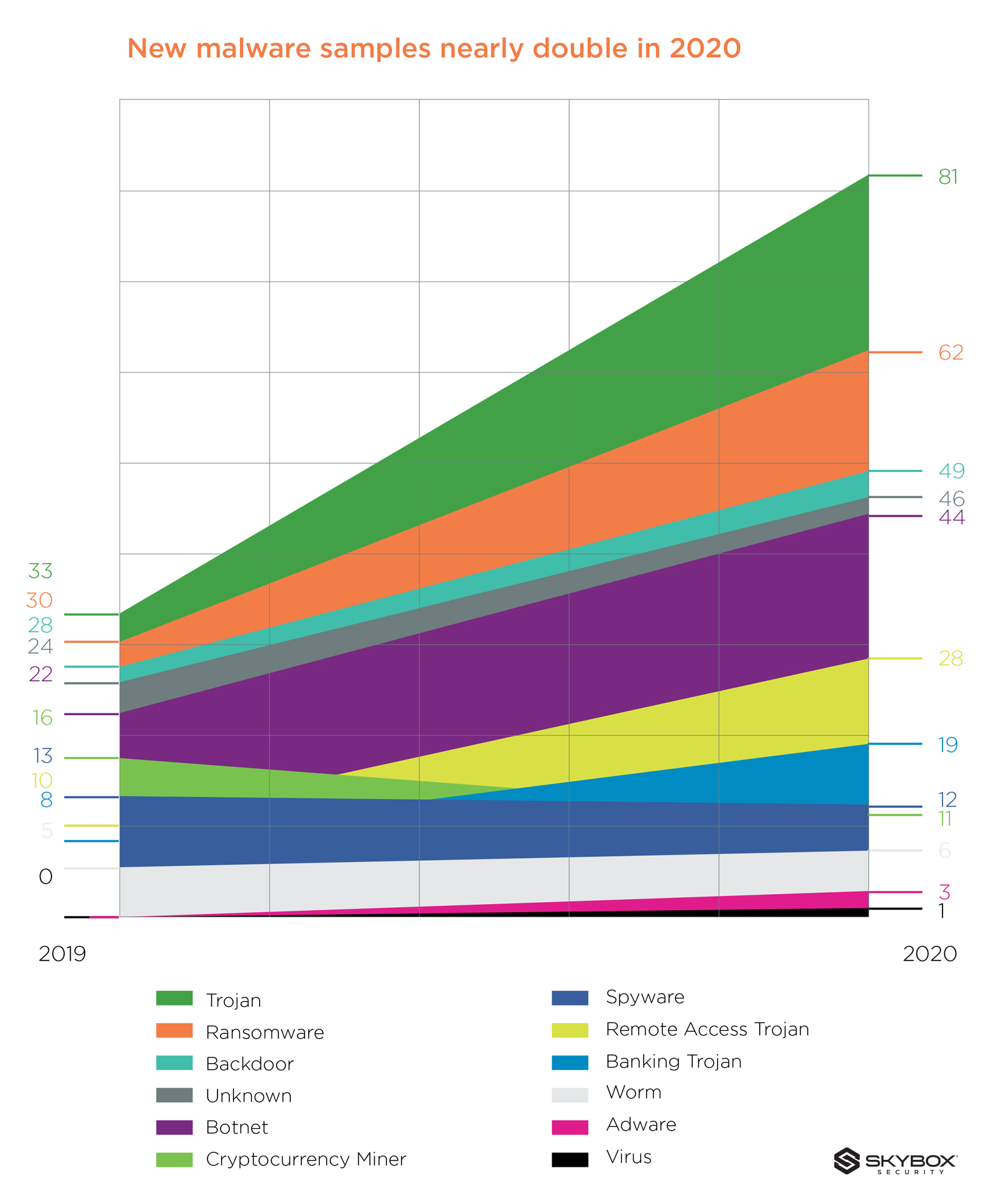
Cybersecurity teams need to evolve their programs so they aren’t operating on a knife-edge. It’s possible to reduce the anxiety that dominates the modern security leader’s headspace through maturing their security posture management programs. For this transformation to be truly effective, organizations need to gain a deep understanding of the current threat landscape, including insight into how the malware cybercrime industry is likely to evolve.
The race to innovate
Consider how threat actors are developing their tools. It’s like holding a mirror to the corporate world. All innovations used by businesses have also been embraced by malware developers and distributors. There will always be relative technological parity between the two parties – this isn’t a race that organizations can hope to win. But they can work to increase their security programs’ scalability in anticipation of further innovation and disruption.
Like the organizations that they target, threat actors are also continuously working to identify new revenue streams. In recent years, we have seen the development of malware-as-a-service (MaaS) models. These are malware packs that can be bought off-the-shelf on the dark web, just like normal IT software is purchased. Inevitably, the MaaS a model that will gain traction because it drastically lowers the technological bar to carry out attacks. And they work in a very similar way to widely-adopted software-as-a-service (SaaS) products. The malware is nicely packaged and is instantly ready for use. Although you would still need to know how to deploy the malware, you no longer need to possess the technical skills required to write the exploit itself.
MaaS wouldn’t exist if it weren’t profitable: Threat actors always chase the money. It’s widely accepted that cybercriminals mainly turn a profit with ransomware when it’s used in targeted attacks, whether they be on government agencies, critical infrastructure, or large enterprises. It is, therefore, possible to infer that confidence in the potential success of ransomware attacks is increasing. This is a testament to the sophistication of both the malware itself and the exploit tactics used by threat actors.
In practice, this means that it’s now easier than ever for bad actors to carry out attacks. It also means that we are likely to see an increase in attacks targeting businesses.
Zero in on what matters
So, what can be done? Among other things, cybercriminals take advantage of traditional security practices that rely on scanning. They count on overworked, overloaded security teams who can’t possibly patch every vulnerability. Organizations need to take a new approach to security posture management – one that is centered on exposure analysis.
Exposure analysis is only possible when disparate data repositories – such as patch and asset management systems, configuration data, threat intelligence feeds, and device data – are brought together with data normalized and modeled. This can be achieved with a network model that understands all devices, vulnerabilities, configurations, and security controls – delivering a dynamic representation of hybrid environments across corporate networks, private cloud, public cloud, and OT.
It also requires multi-factor risk prioritization that supplements scanning data with third-party data such as EDR, CMBD, network connectivity, OT security, threat intelligence, and more. This analysis must also consider whether a vulnerability has been exploited in the wild. In fact, our Skybox Research Lab tracks tens of thousands of new vulnerabilities yearly on more than 8,000 products to provide this data to customers.
Through taking a new approach to exposure analysis, it is possible for organizations to stay one step ahead of cybercriminals. By optimizing remediation strategies to focus on the highest exposure risk, they can address the rise in vulnerabilities, expanding attack surfaces, sophisticated threat actors, and talent shortages.





