A recent Microsoft patch for a zero-day vulnerability in Microsoft Outlook (CVE-2023-23397), highlights the importance not only of regular patching but also of having a range of remediation options at hand.
Outlook for Windows Users are Vulnerable
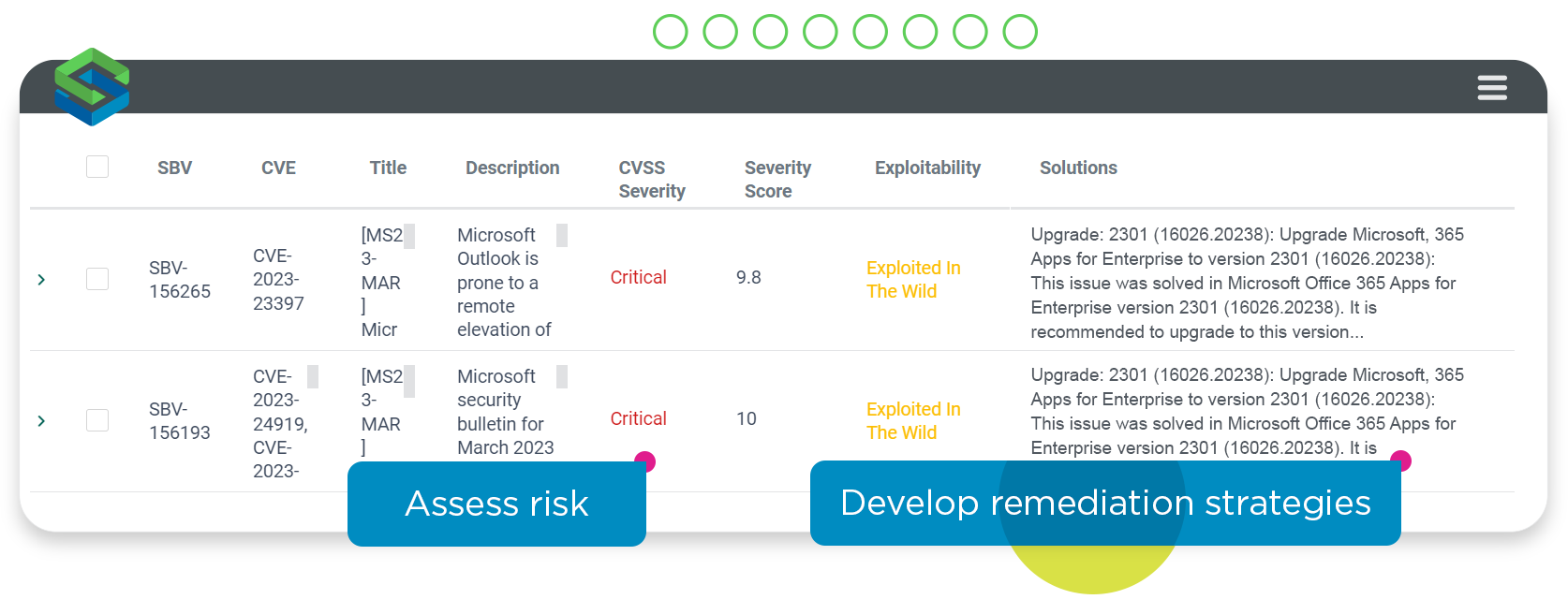
CVE-2023-23397 is a vulnerability in Microsoft Outlook that has the potential to grant an attacker the ability to perform a privilege escalation. The vulnerability affects installations where Outlook for Windows desktop clients are connecting to an Exchange server. It enables attackers to steal the NTLM hashes used in the authentication process, and re-use them, passing themselves off as the user to conduct other malicious activity such as continued lateral movement within the network, the installation of malware or the theft of corporate data.
Microsoft has issued a patch for the vulnerability, but there’s increasing evidence that it will be exploited in the wild and what makes it noteworthy is that it requires no specific action on the part of the user. Merely being in receipt of a compromised Outlook message is enough to trigger the exploit. It is not necessary to open the email or view it in the preview pane, to initiate the compromise.
With such a large install based of Outlook for Windows clients and a vulnerability that can be exploited without any specific action on the part of the user, there’s the potential for CVE-2023-23397 to have widespread ramifications. Fortunately, Skybox Security customers have a range of capabilities available to them to help mitigate the threat.
Use the Skybox Threat Intelligence Service
The Skybox Vulnerability & Threat Management solution includes Skybox Threat Intelligence, a service that notifies customers of vulnerabilities and in this case, the CVE was flagged within hours of the vulnerability being made public.
Assess prevalence and exposure
Using Skybox Vulnerability & Threat Management, customers can assess both the prevalence of the vulnerability across their IT estate and the extent of their exposure.
In terms of prevalence, if a customer has patch management data, for example from Microsoft System Center Configuration Manager (SCCM) integrated into Skybox, they can use the Skybox Vulnerability Detector to scanlessly identify the existence of the Outlook vulnerability on an asset because of the absence of the required patch.
In addition, Skybox Vulnerability & Threat Management provides the ability for customers to analyze occurrences of the vulnerability within their infrastructure in terms of asset importance, exploitability, and exposure.
Block TCP outbound via Port 445
In situations where it is not possible to patch promptly, Skybox Security customers can ensure an additional layer of protection by using Skybox Firewall Assurance to combat the risk that the vulnerability could be used by attackers to route the NTLM hashes to external file servers.
Customers can check across the attack surface, analyzing firewall access and blocking TCP outbound over port 445 to the Internet to block the exfiltration of NTLM authentication hashes to file servers controlled by the attackers.
Segment the network to protect critical user accounts
Customers with Skybox Firewall Assurance and Network Assurance can also use the Trusted and Untrusted Zones capability to enforce a network segmentation policy that ensures critical user accounts are grouped in a zone where TCP outbound over port 445 is prohibited.