2261 Market Street, #5605
San Francisco, CA 94114-1612
- Continuous Exposure Management Platform
- Vulnerability Control
- Firewall Assurance
- Network Assurance
- Change Manager
Continuous Exposure Management Platform
Continuously assess, prioritize, and remediate the cyber threats that matter most across your hybrid attack surface. Focus security teams where they can make the most impact.
What is the Skybox exposure management platform?
The Skybox platform supports each stage of your enterprise’s continuous exposure management program to map the attack surface and contextualize with data, assess and prioritize vulnerabilities, and combat the threat through final remediation. Integrated attack surface management, vulnerability management, and security policy management solutions make it easy to manage exposures and maximize the effectiveness of your security team.
The Skybox platform drives exposure management programs
With Skybox, you create consistent, enterprise-wide exposure management programs that continuously map your attack surface, contextualize the results, assess and prioritize the threats, and automate remediations to combat them. The power of our platform is built on the aggregated security, policy, and infrastructure data collected and aggregated from your infrastructure and cloud environments. With Skybox you will achieve greater insight, make smarter decisions, build business resiliency, and maximize your valuable technical resources on what matters most to your organization.
Solutions

Attack surface visibility and management
The Skybox platform meticulously curates a robust network model and inventories your assets, networks, clouds, and users to manage cyber risk across your organization’s hybrid attack surface.
Through advanced techniques like attack path analysis and simulation, we detect, prioritize, and combat internet-accessible threats. We illuminate potential exploit routes, scrutinizing firewall and network configurations to identify vulnerabilities.
The result is strategic visualization and detailed reports of your hybrid attack surface, empowering your organization to proactively monitor, track changes, and swiftly respond to emerging threats.
Vulnerability management
Skybox leverages an array of 3rd party threat intelligence sources, and our own Skybox Threat Intelligence, to enrich your attack surface map and provide a holistic view of your vulnerability and threat exposure. Our multi-factor risk assessment and prioritization considers severity, importance, exploitability, and network exposure, enabling you to focus resources on vulnerabilities that represent the most risk to your business.
Beyond prioritization, Skybox offers proactive, automated remediation suggestions and controls for each vulnerability. We facilitate streamlined responses through ITSM system integration, network segmentation recommendations, and automated firewall adjustments. Even without immediate patching, Skybox Vulnerability Control provides effective risk mitigation alternatives.
Security policy management
Gain deep insights into your network, analyzing configurations, paths, connectivity, and access. Skybox Network Assurance ensures meticulous adherence to proper network zoning, bridging any gaps that may exist between your official network segmentation policy and the actual implementation within your hybrid network environment.
Skybox Firewall Assurance optimizes performance by identifying and eliminating shadow or redundant firewall rules and managing numerous firewalls through a centralized interface. Skybox Change Manager automates firewall changes, with risk assessments conducted before provisioning new rules. Easily recertify firewall rules and generate reports vital for compliance audits. Harness the power of efficient network management, bolstering your cybersecurity while maintaining compliance.
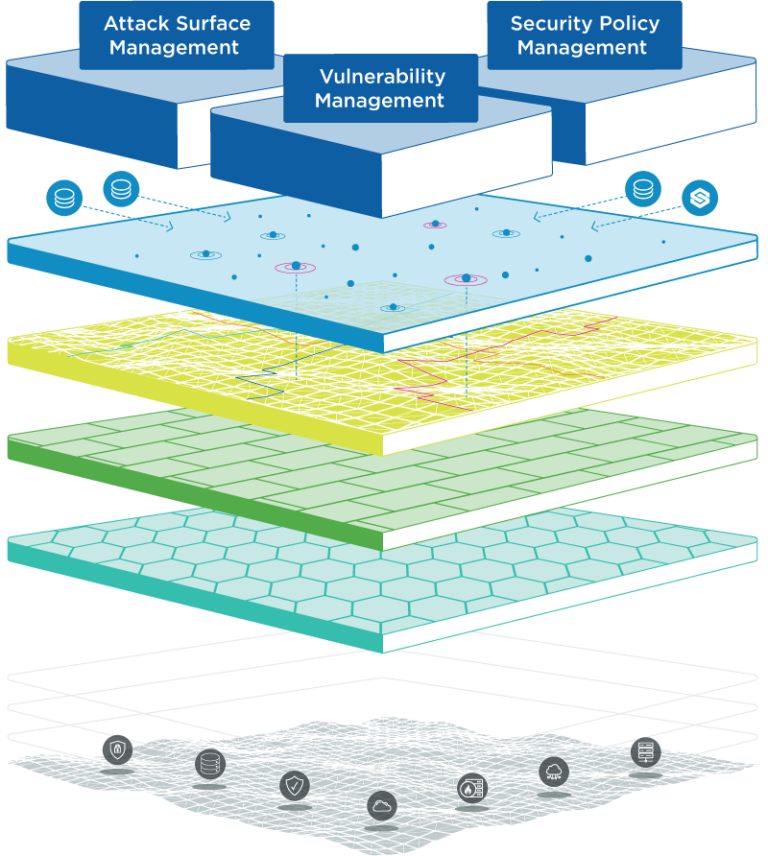
Skybox Dynamic Security Model
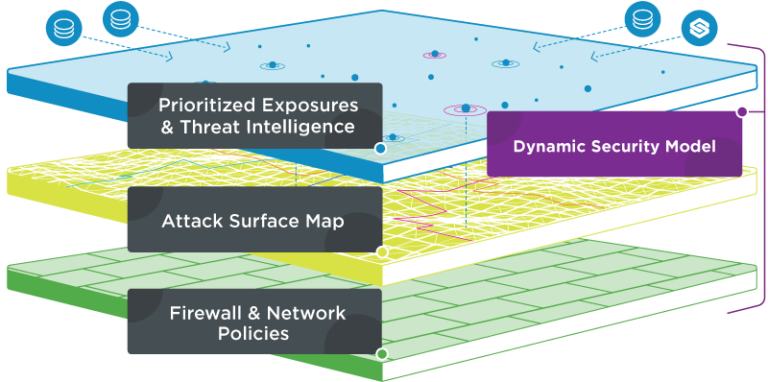
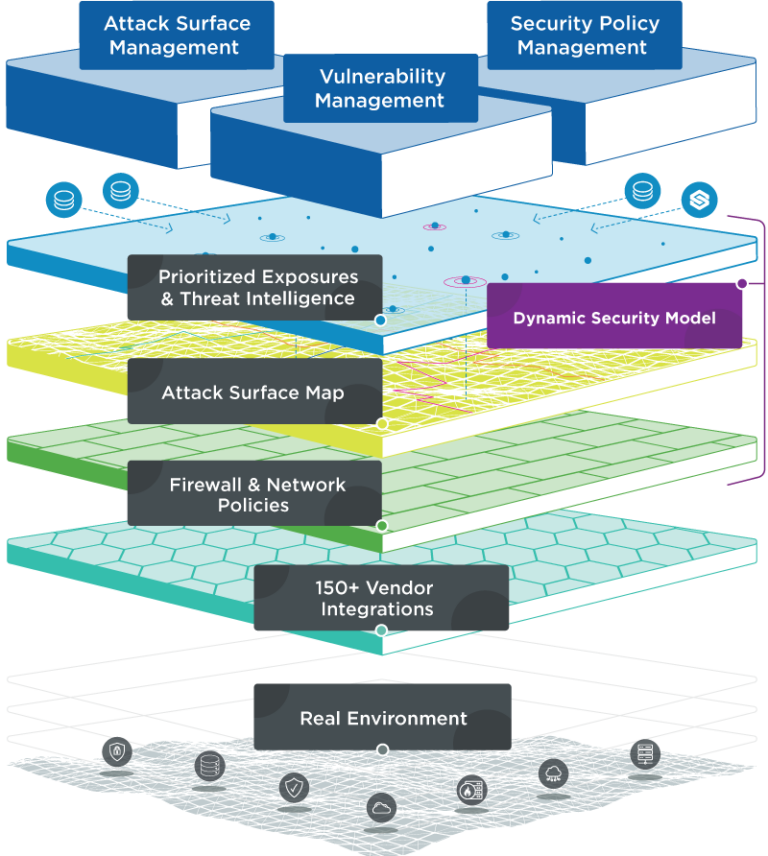
Exposure Management starts with a robust model
Skybox’s dynamic security model provides a 360-degree hybrid attack surface map, built on a comprehensive understanding of firewall and network security policy, and overlayed with threat intelligence and risk data for enhanced cybersecurity and automated remediation. The model integrates asset information, vulnerability and threat data, network and security controls, and insights into applications and users for a panoramic view of your entire attack surface.
Use the model to analyze potential attack paths, fine-tune security policies, and prioritize your defenses. Insights on vulnerability severity, asset importance, and exploitability gleaned from Skybox Threat Intelligence enable prioritized risk management. Continuously updated, the model delivers actionable remediations and automated controls to fortify your security.
Threat Intelligence & Prioritized Exposures
Skybox aggregates 35+ intelligence feeds into our Threat Intelligence Service, including vulnerability scanners, vendor advisories, IPS signature updates, public databases such as NIST NVD, exploitability notifications and expert advisories, including MITRE CVE, CISA, CERT and ICS CERT.
Assess and prioritize exposures based on not only CVE severity, but also the importance of the asset to the business, evidence of exploitability in the wild, and exposure of the asset to potential compromise across the hybrid network.
Attack surface map
You can’t protect what you can’t see. For a complete picture of your organization’s exposure, you need a detailed attack surface map showing all the assets, networks, clouds, applications, users — and the routes and attack paths between them.
Firewall & network policies
Some of the most critical exposures and risks that an organization faces are not caused by vulnerabilities. They’re a function of missing network security controls or device misconfigurations.
A detailed insight into the underlying infrastructure, network, and security policy, enables you to understand how the network is segmented and zoned and analyze firewall configuration and rule bases for potential security gaps.
Simplify policy management, control large numbers of firewalls from multiple vendors from a single interfaces, assess firewall change requests, and automate changes that reduce exposure.
150+ vendor integrations
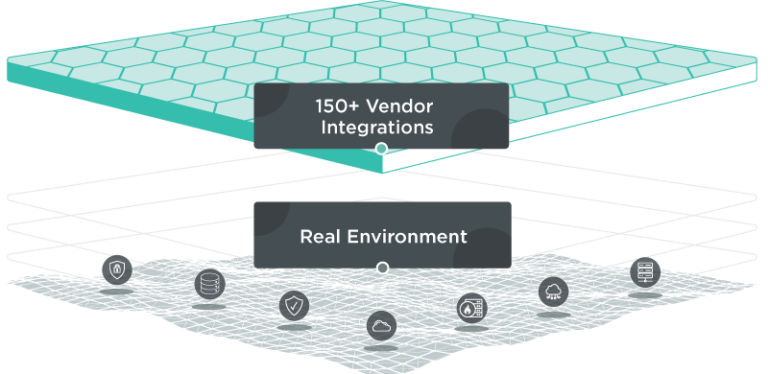
Broad ecosystem integration and data aggregation
Skybox’s hybrid attack surface model aggregates data from over 150 integrations, including leading network platforms, asset databases, and security technologies. The model holds information on the devices, applications, and users in the organization, as well as:
route, access, and permission metadata
security control, patch, and XDR data
vulnerability and threat scanner data
These insights empower risk-based and prioritized vulnerability management.
Real Environment
The model draws on data from across the real environment, including Network infrastructure, Firewall and IPS, CMDB, Cloud infrastructure and security, XDR data, Vulnerability scanners, OT security, LDAP, and more.
Remediation and change automation
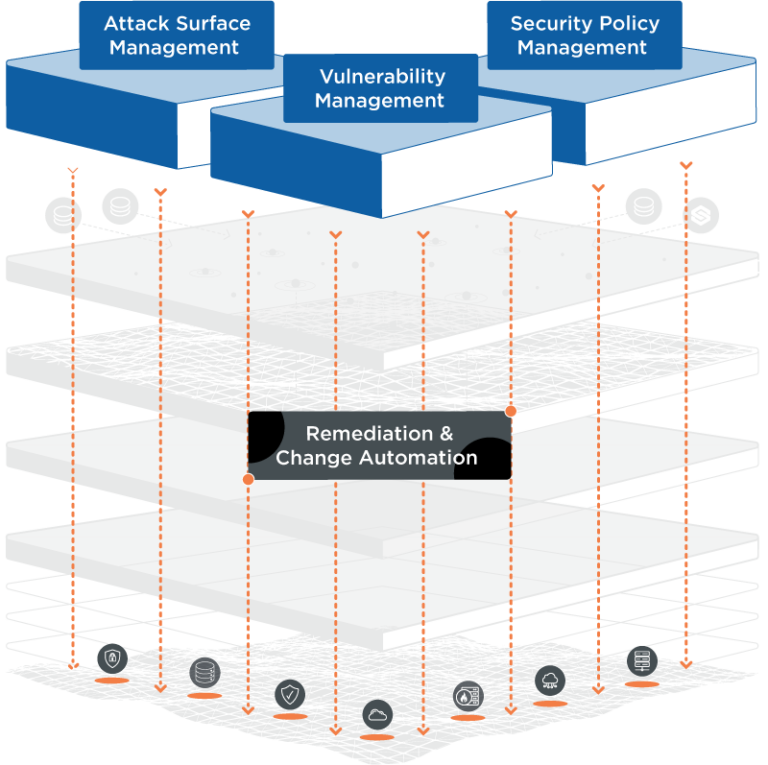
Quickly mitigate risks and trigger remediation processes, leverage seamless automation with your ITSM system to speed up ticketing, inform patch cycles, and maintain accountability with comprehensive audit trails.
When the cadence between patching cycles exposes a vulnerable asset to compromise for too long, Skybox automatically suggests alternative compensating controls, such as changes to network segmentation, the application of IPS signature updates, or modifications to firewall rule tables.
Use change automation workflows to automatically maintain security policy compliance. Manage firewall rule recertification, change verification, and de-provisioning.
Skybox empowers organizations to achieve Continuous Exposure Management
The Skybox platform enables your organization to quickly implement or enhance a continuous exposure management program.
Get a customized platform demo, or learn more about how Skybox can help:
Skybox Cloud Edition
Now there are no limits
Skybox Cloud Edition is the world’s first “Software-as-a-Service” (SaaS) continuous threat exposure management platform for attack surface, vulnerability and network security and policy management that is managed in the cloud.
Faster time to value
With rapid on-boarding from a dedicated Skybox team and instant access to the latest innovations as they become available.
Guaranteed service levels
Including 99.5% solution availability and reliability, limitless scalability, and continuous monitoring by Skybox experts.
Lower costs of ownership
Reduce reliance on on-premise infrastructure, eliminate operational maintenance costs, and cut training budgets.
Take advantage of the first complete SaaS offer for managing security policy and vulnerability risk prioritization in hybrid environments with these scalable, modern solutions.
Related resources

Continuously assess, prioritize, and remediate exposures across your hybrid attack surface. Get the Skybox platform brochure.
Understand how continuous threat exposure management (CTEM) programs provide the visibility and context organizations need to prioritize exposures and mitigate risk.
Understand why leaders are quickly embracing the CTEM model to bolster their cyber risk reduction strategies.
Reduce cyber risk across your hybrid attack surface with the Skybox Continuous Exposure Management platform.
Let’s talk
Would you like to discuss how your organization can achieve Continuous Exposure Management?
Get started
Share your requirements, and we’ll take you on a customized, guided demonstration to show how Skybox can help.

