The year was 1999. Alongside the launch of the Euro, the debut of the Sopranos, and The Matrix premiere was an initial concept to track all vulnerabilities known. The Common Vulnerabilities and Exposures (CVE) list was launched in September 1999 with 321 CVE records. A few years later, at the beginning of 2005, CVSS scoring was established to provide standard, open-source severity ratings of software vulnerabilities.
In the early 2000s, most organizations could manage the vulnerability list independently; a list could be managed with a spreadsheet generated from a one-off scan of the network. But over the last 20 years, the number and complexities of vulnerabilities have increased exponentially, with nearly 200k tracked vulnerabilities by 2023. We no longer live in a world where a periodic scan is enough to keep you secure.
Today, the vulnerability spreadsheet for an organization usually has many thousands or even millions of instances. New vulnerabilities are being identified at an alarming rate, and too much risk persists between scheduled scans, much less the long delays between patching cycles. This complexity is why many organizations move beyond traditional scanners to continuous vulnerability management tools for increased visibility and better security.
What is vulnerability and threat management?
Organizations now need a modern vulnerability and threat management (VTM) solution. Unlike vulnerability scanning, which only focuses on discovery, severity, and patching, true vulnerability management programs provide more. Vulnerability management program best practices today recommend organizations continuously evaluate, treat, and report on the security vulnerabilities in their environment to stay ahead of the ever-changing threat landscape.
|
Vulnerability Scanners |
Modern Vulnerability and Threat Management |
| Assess |
Snapshot in time of a subset of assets |
Continuous, unified view of your entire hybrid attack surface |
| Discover |
Vulnerabilities periodically found by an installed agent on scannable assets to identify hardware, software, and systems |
Scannerless vulnerability detection continuously evaluates all assets for vulnerabilities — including unscannable assets, such as air-gapped networks or OT devices |
| Prioritize |
Based only on CVE severity |
Calculates business-specific risk including network accessibility and attack path analysis, the exploitability of the vulnerability, and the business importance of the asset |
| Remediate |
Patching only |
Prescriptive compensating security controls to mitigate risk between patching cycles |
| Report |
Limited reporting capabilities |
Continually monitors for changes in exposure and exploit activity |
Why is vulnerability and threat management important?
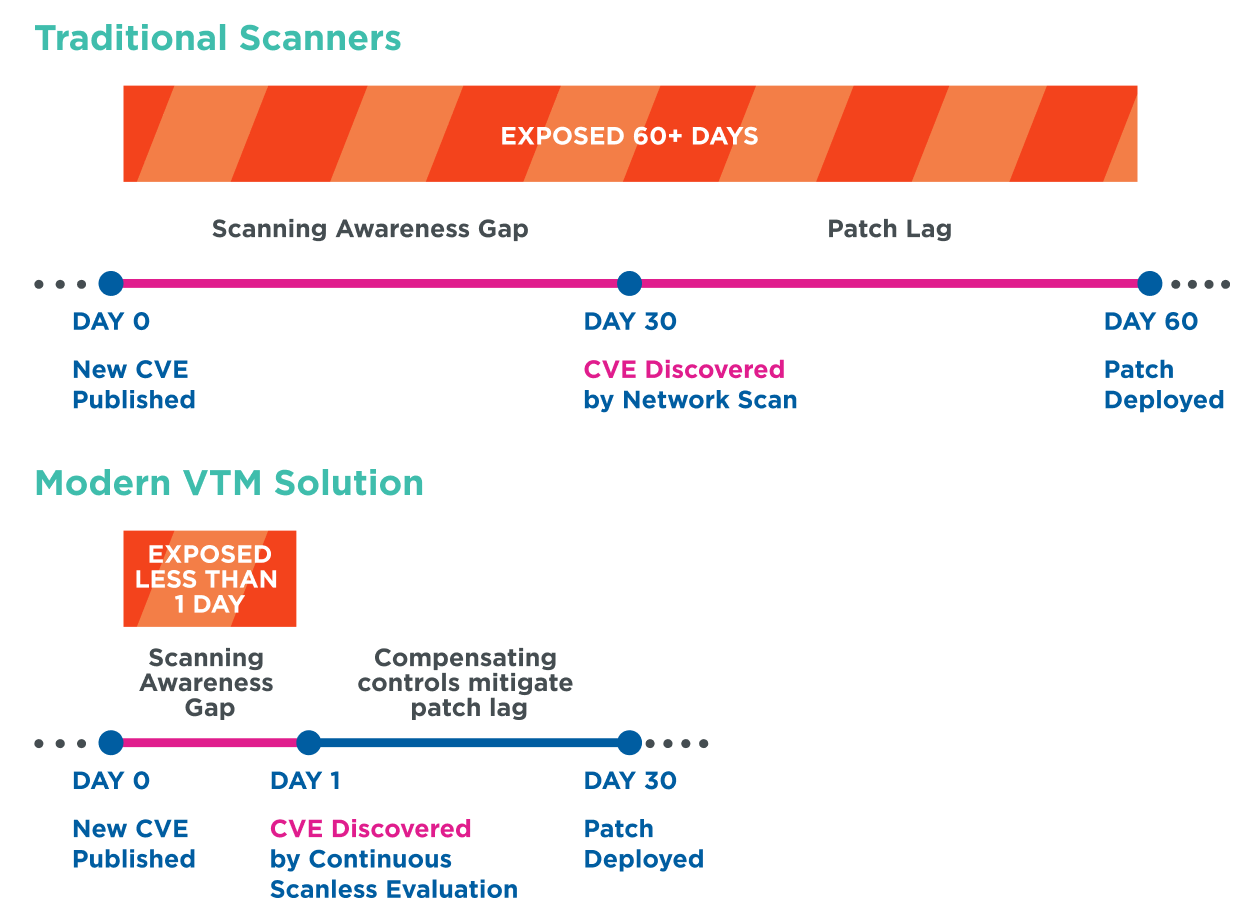
A recent report by scanner vendor Qualys has shown that a quarter of security vulnerabilities are immediately targeted for exploitation, with the exploit being published on the same day as the vulnerability was publicly disclosed. Since most organizations perform asset scanning every 30 days and only after this do they patch the identified vulnerabilities (often weeks to months later), this typically means they have a turnaround time of approximately 60 days for patching.
On the other side of the coin are cybercriminals who work quickly. On average, an attacker needs less than 80 minutes after the initial compromise to launch an attack on other systems on a network. So, if a vulnerability is already exploitable on the day it is disclosed, an organization will remain vulnerable to critical threats for months – and that’s a lot of time for a cybercriminal to cause damage.
This is why organizations must look for a vulnerability and threat management tracking system that will complement their current security stack and provide continuous visibility of their networks to help them mitigate risk.
What makes an effective vulnerability and threat management solution?
With so many solutions on the market saying they do vulnerability management, it’s often hard to differentiate the platforms that will effectively help you manage your ever-growing list of vulnerabilities. The key to a successful vulnerability management solution is that it’s actionable, accurate, continuous, and based on centralized, normalized, and complete data sets.
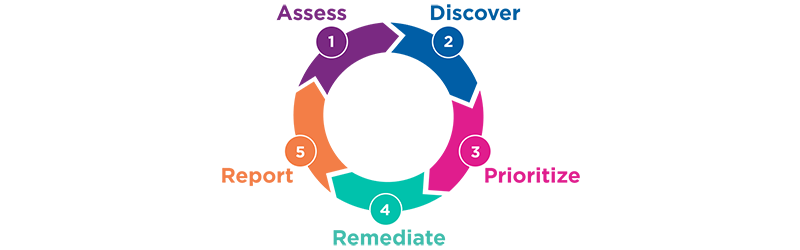
Vulnerability management program best practices should involve five phases:
- Assess your attack surface
- Discover potential attack paths
- Prioritize which vulnerabilities are the highest risk
- Remediate the most critical vulnerabilities
- Report back risk and status to stakeholders
These five phases should be included in any vulnerability and threat management tracking system because each step is critical to staying ahead of cybercriminals. An effective solution should also de-duplicate and aggregate scan data from your current security tools, including scanners, and combine it with the latest threat intelligence for a complete picture of your risk. Daily scannerless evaluations allow you to continually evaluate your attack surface, get a manageable list of the highest priority threats, and get a list of compensating controls to mitigate risk between patch cycles.
Skybox Vulnerability Control provides the unique ability to discover, prioritize, and remediate threats from one platform. Our Vulnerability Detector identifies newly disclosed vulnerabilities in relevant assets within 24 hours of their disclosure. Following detection, we conduct an in-depth analysis of the potential for exploitation in our customers’ environment and propose compensating control mitigations where applicable. This comprehensive approach ensures critical/high-impacting vulnerabilities are effectively mitigated within 2-3 days – as opposed to months with traditional scanners.
See how Skybox can help you better manage your vulnerabilities: