Threat Intelligence Service
A single, comprehensive, daily cyber threat intelligence feed aggregating 35+ sources, enhanced with expert analysis of vulnerabilities and remediations, correlated to your specific environment and devices.
For a detailed list of included threat intelligence feeds:

Manage exposure with threat intelligence
A foundational component of the Skybox Continuous Exposure Management Platform, our cyber threat intelligence service enriches both security policy management and vulnerability management programs by providing:
- A comprehensive guide to the latest vulnerabilities.
- Analysis of the assets in your hybrid attack surface hosting exploitable vulnerabilities.
- Knowledge of which vulnerabilities are being actively exploited in the wild.
- Identification of IPS signature updates that could be used to remediate each vulnerability.
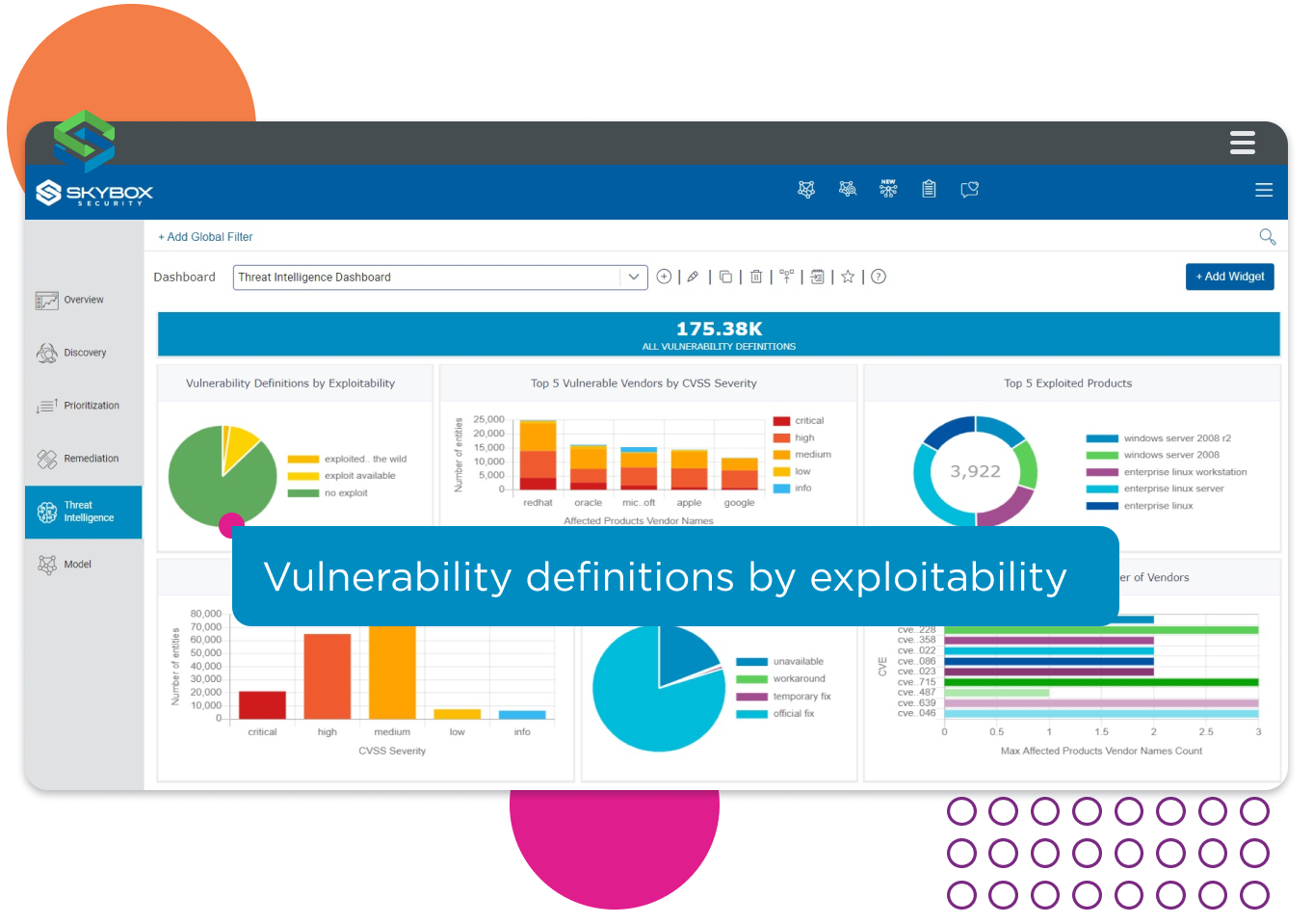
Threat intelligence about vulnerabilities correlated with evidence of exploitability.
Start with definitive threat intelligence
Skybox threat intelligence is carefully curated to provide a definitive reference for both security and network infrastructure professionals. Identify vulnerabilities in standard operating systems, browsers, software, databases, firewalls, and network devices using aggregated threat intelligence from over 35 separate sources, including:
- Vulnerability scanners and vendor advisories.
- Public databases (NIST NVD) and exploitability notifications.
- Solutions from IPS signature updates.
- Expert advisories and insights from the Skybox Research Lab.
Instantly identify vulnerable assets
Daily updates provide an exhaustive analysis of exploitability for each vulnerability. Use the intelligence to identify which assets in the estate host vulnerabilities that are currently being exploited and even predict the likelihood that a vulnerability will be actively exploited in the future. Instantly identify:
- All assets with vulnerabilities, even assets on air-gapped networks or without scanners.
- Celebrity vulnerabilities and the assets hosting them.
- Internet-facing assets with vulnerabilities that are being actively exploited in the wild.
- The malware name and category associated with an exploited vulnerability.

Instantly identify assets vulnerable to celebrity exploits and vulnerabilities.
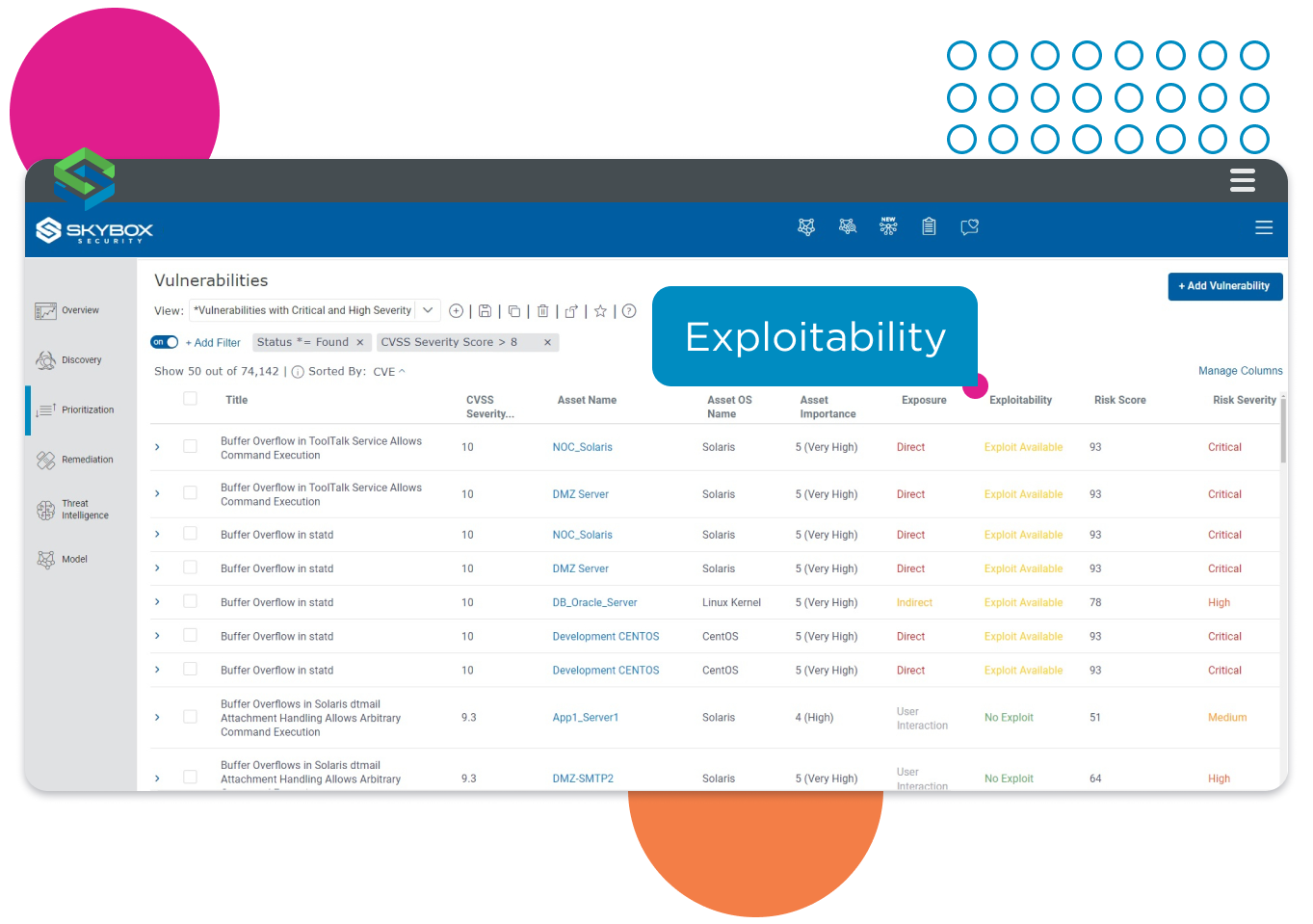
Incorporate evidence of exploitability in multi-factor prioritization.
Understand exploitability to enhance vulnerability prioritization
Current and likely future exploitability analysis from the Threat Intelligence feed is automatically incorporated into Skybox’s multi-factor prioritization, along with an assessment of CVSS severity. This analysis is then enriched with customer-specific analysis of the business impact of asset loss and the extent to which an asset is accessible to attack across the network.
Risk-scoring each vulnerability using this multi-factor approach provides a standardized mechanism for prioritizing vulnerabilities, focuses the team on those that matter most, and helps protect the organization from attackers.
Analyze attack paths
By overlaying the latest threat intelligence onto your attack surface map, Skybox provides insights into how network access paths could be used by attackers to compromise a vulnerable asset. This intelligence is essential to the analysis of potential attack paths and for attack simulations, enabling analysts to identify:
- Reachable network attack paths an attacker could use.
- Vulnerabilities along each route.
- Evidence of exploitability for each vulnerability.
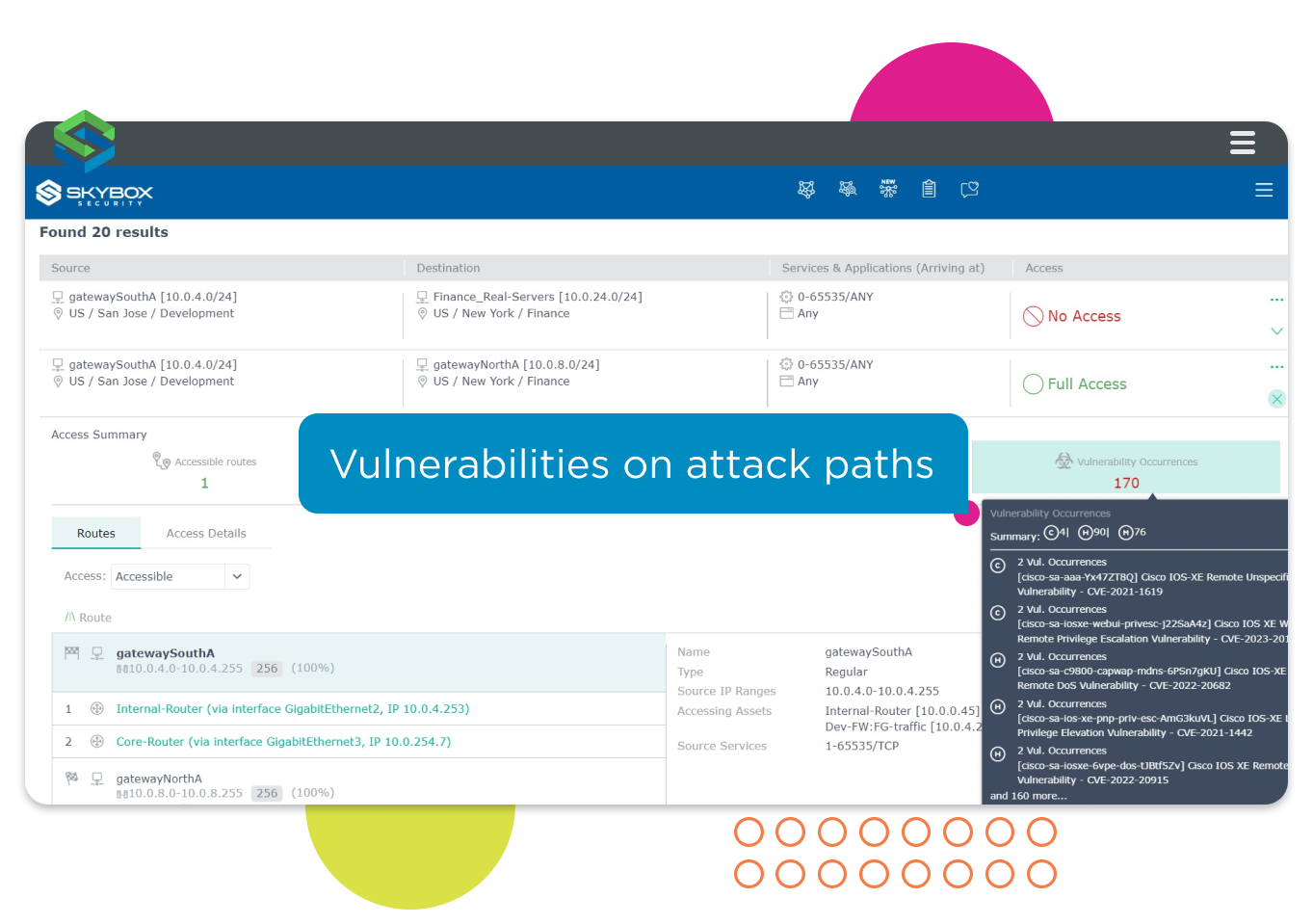
Analyze attack paths for evidence of vulnerabilities.
Related Skybox Products
These Skybox products include the Threat Intelligence Service, enabling you to proactively identify vulnerabilities that could pose a significant business risk.

Threat intelligence about vulnerabilities correlated with evidence of exploitability.

Instantly identify assets vulnerable to celebrity exploits and vulnerabilities.

Incorporate evidence of exploitability in multi-factor prioritization.

Analyze attack paths for evidence of vulnerabilities.