Security Policy Management
Centralize the management of your firewall and network policies for better security. A Network Security Policy Management tool collects, normalizes, and optimizes network and security data for comprehensive visibility, control, and insights.

With a Network Security Policy Management solution, you will:
- Simplify complex firewall and network policy management
- Gain full visibility across your hybrid networks
- Automate change management to reduce errors
- Maintain continuous compliance
Streamline your firewall security policy management
Managing a large network of firewalls is a challenge for any team. With an NSPM solution, you take control of your firewall security policy management. Complete...
Managing a large network of firewalls is a challenge for any team. With an NSPM solution, you take control of your firewall security policy management. Complete visibility to your complex multi-vendor environment powers you to analyze rules, optimize security policies, and manage changes to eliminate the complexity of firewall management and reduce overhead costs.
Network and IT teams often face a high volume of change requests in order to maintain their networks at optimal levels. Automating change management workflows enhances...
Network and IT teams often face a high volume of change requests in order to maintain their networks at optimal levels. Automating change management workflows enhances business agility by expediting firewall rule provisioning and freeing up staff time for crucial priorities.
An NSPM solution ensures continuous compliance and audit readiness across your networks by properly configuring your firewall rule bases. This not only aligns your organization’s security...
An NSPM solution ensures continuous compliance and audit readiness across your networks by properly configuring your firewall rule bases. This not only aligns your organization’s security and compliance policies but also optimizes performance, so you confidently go into your audits.
Maximize protection with a network security policy management program
Firewalls act as gatekeepers into your networks. Having clear and concise rules around network access and changes keeps your organization secure. However, with the rapid growth of so many companies, firewall rules often grow out of control. One small misstep or misconfiguration leads to disaster – violations, fines, outages, or even data breaches. This is why organizations are turning to network security policy management to take control of their networks.

The six phases of an effective NSPM program.

Aggregate & normalize data for a single source of truth
Because most organizations today have many thousands of systems on their networks, it is difficult to aggregate all of that data into a single source of truth. The constant revolving door of servers and devices being added, removed, upgraded, consolidated, distributed, virtualized, and moved to the cloud leads to duplicates or conflicting information from different sources and vendors. This leaves the nearly impossible task of maintaining an accurate, up-to-date model of their network connectivity, access, and topology.
This is where a network security policy management solution (NSPM) tool is important. Rather than taking months to manually collect and assemble, an NSPM tool ingests and normalizes data from all L3 network devices, public and private clouds, software–defined data centers, and OT networks, so your data is all in sync. This allows you to correlate all access control lists, security tags, routing rules, NATs, proxies, VPNs, and more, as well as troubleshoot network connectivity problems and identify root causes – all from a single solution.
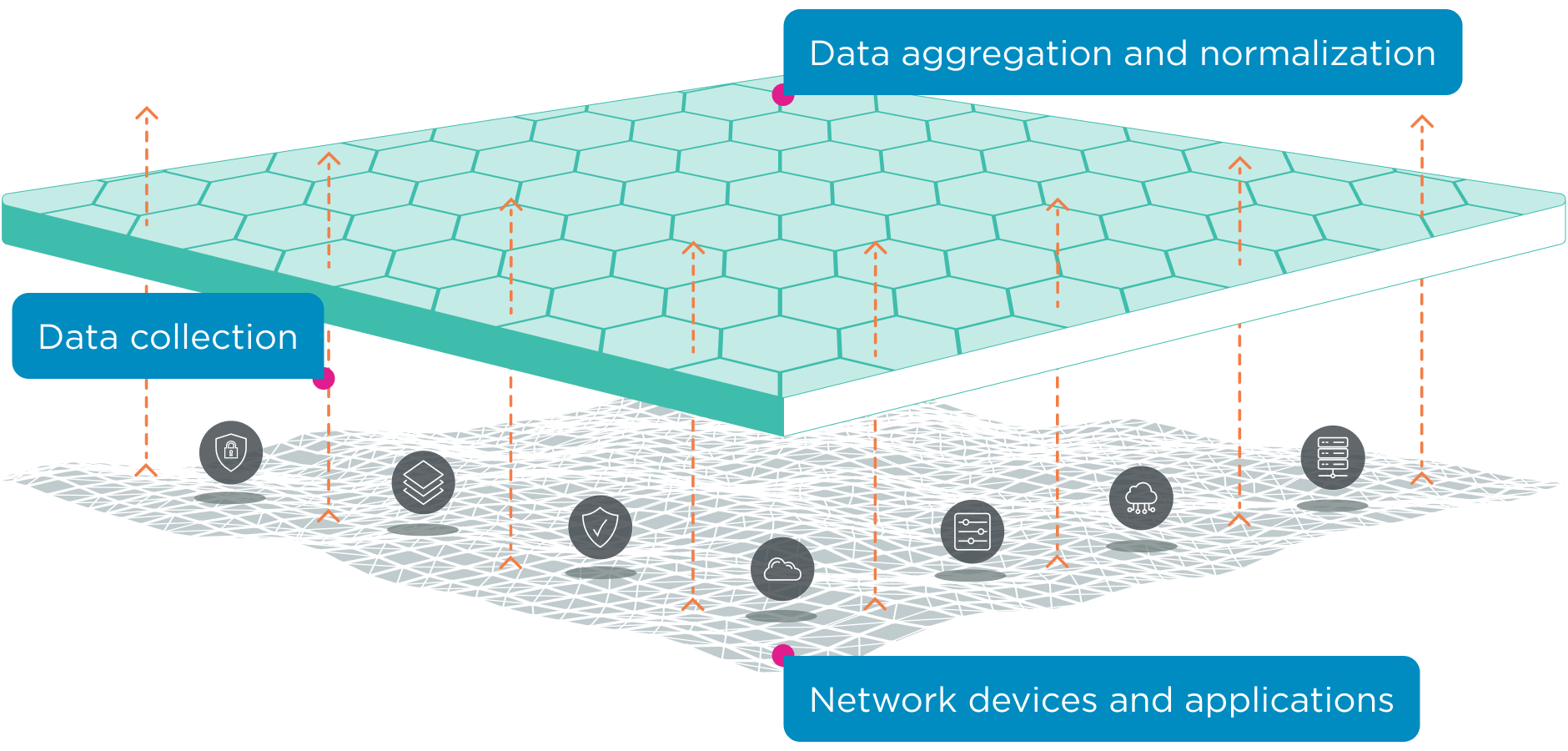
An NSPM solution collects and aggregates data from different devices in your network.

Build a detailed map of your network, combining asset information with network topology, infrastructure data, security, and threat intelligence.

Discover & visualize your network for optimal security
Managing your firewalls is a crucial aspect of a Network Security Policy Management (NSPM) solution. An efficient NSPM tool builds a comprehensive network topology map, covering hybrid, multi-cloud, and OT networks.
This map helps you better understand your network topology and enables you to perform end-to-end access analysis. In this map, you define zones, view access routes, and understand how traffic enters your most important zones, so you better defend against potential attacks on critical assets.
Normalized data from all Layer 3 devices, public and private clouds, and OT networks, also helps you quickly identify any vulnerabilities lurking in your network to help you stay on top of threats and better mitigate risk.

Analyze & clean up firewall rules for improved security hygiene
In many organizations, when firewalls or rules are added or modified, few steps are taken to minimize overlap or redundancy. Organizations without firewall management software end up with a bloated system, introducing unknown risks over time. NSPM tools make complex policy management easier, faster, and more effective. As a vendor-agnostic solution, they act as a single pane of glass to continuously review and monitor your firewalls for network connectivity and security policy violations.
On-going reviews of firewall rules help organizations clean and optimize their networks. This process looks for:
- Shadowed, redundant, expired, or disabled rules
- Duplicate or orphaned objects
- Unused rules/objects
- Partially used rules/objects
See how a multinational retailer improved their cyber hygiene:
Discover the six steps to optimize firewalls:
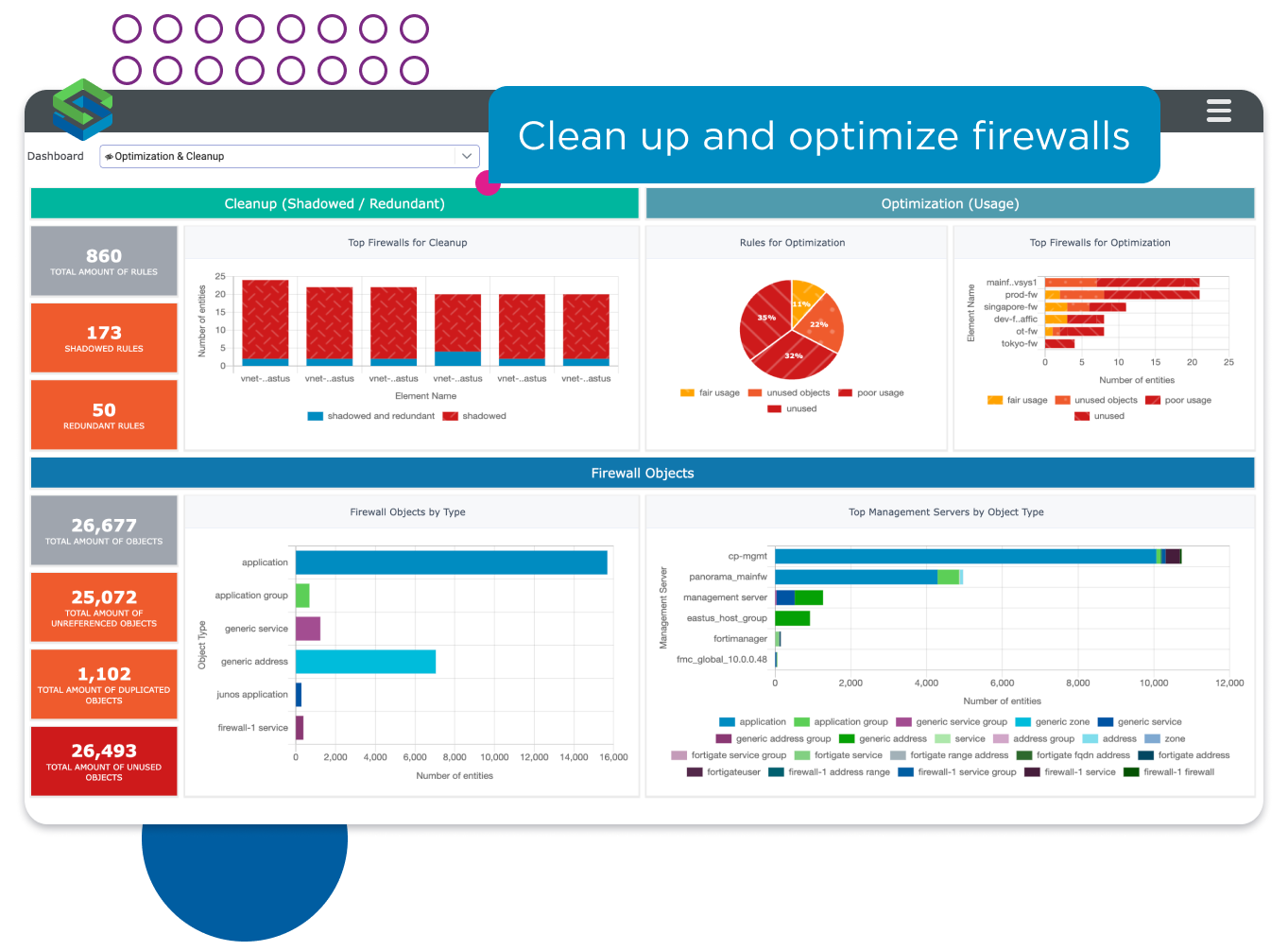
Quickly identify unnecessary firewall rules to clean and optimize your network.
Provision firewall rule changes all from a single platform

Provision & validate rule changes quickly and easily
Proper firewall rule management not only makes you more efficient, but it is an essential part of securing your organization. However, manual firewall rule management is time-consuming and error prone. With an NSPM solution, you directly provision firewall rules from a single platform. This near “zero-touch” approach makes it much easier to add, modify, or delete rules on your firewalls and validate rules against your organizational policies. The repeatability of the process means you are less likely to make mistakes than with manual tracking via emails or spreadsheets.
With the press of a button, an NSPM solution makes changes to your firewalls, using the same connector it uses to manage the firewall rules. Changes include:
- Adding a new firewall, or decommissioning an old firewall
- Reviewing and changing firewall rules
- Validating firewall rules against policies

Automate & orchestrate change management to streamline workflows
Keeping up with the inundation of complex rules and configuration changes for firewalls often leads to quick actions and a lack of proper documentation. For most teams, this is a daunting task. But what if it doesn’t have to be?
NSPM removes redundant manual and error-prone processes by creating automated workflows of established actions and orchestrating them through integrations with your on-prem or cloud firewall vendors. This frees up your team’s time for other high-priority tasks and creates consistency in processes, reducing the chance of misconfigurations or other human errors.
Automation of firewall change management workflows include creating tickets for rule or object deletion or modification, recertification, and automated provisioning of rule or object changes on firewalls. Your NSPM solution should also provide a risk assessment for any proposed changes so you understand the possible business risks introduced before you make the changes.
Learn more about Skybox automation:
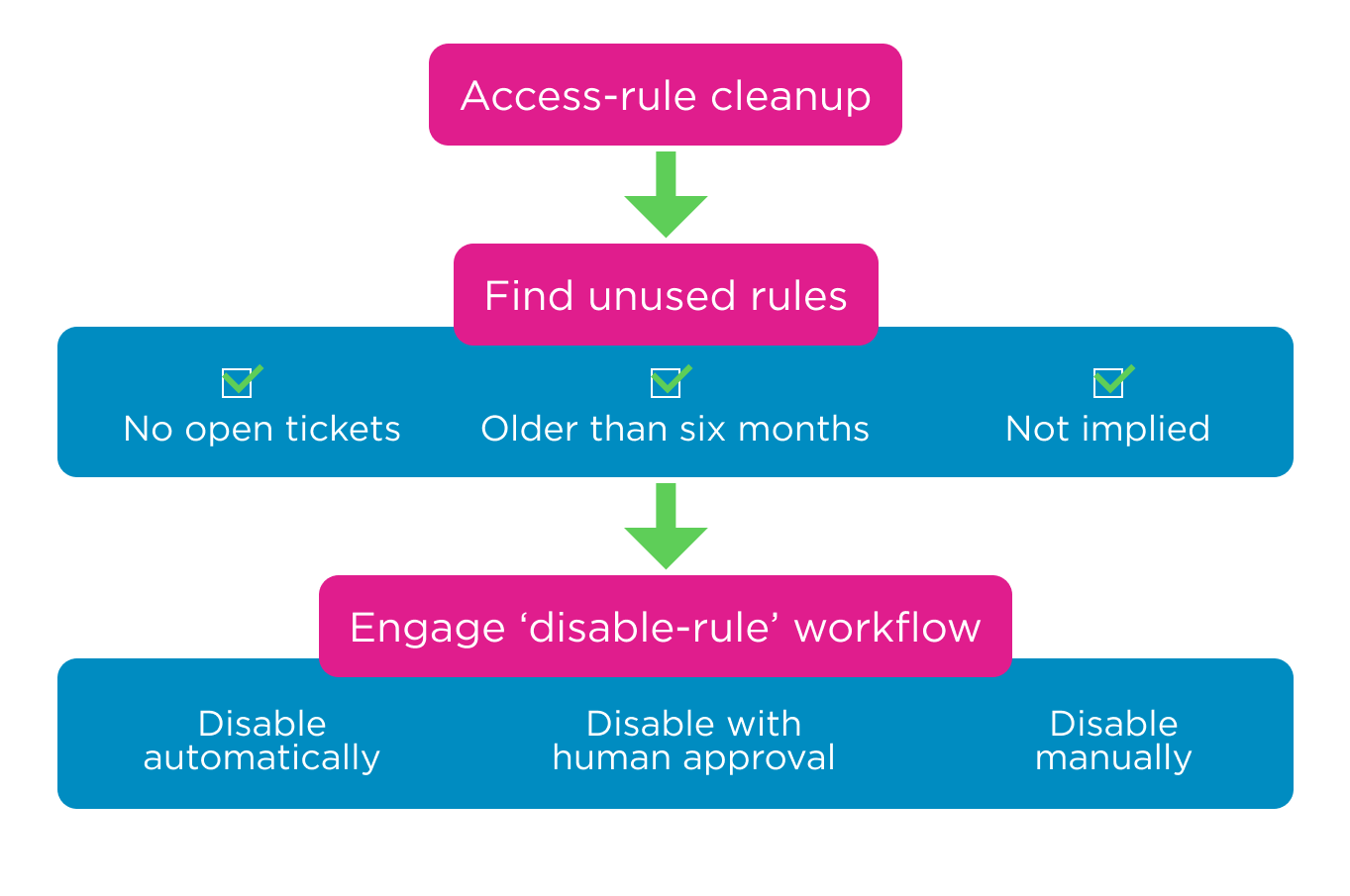
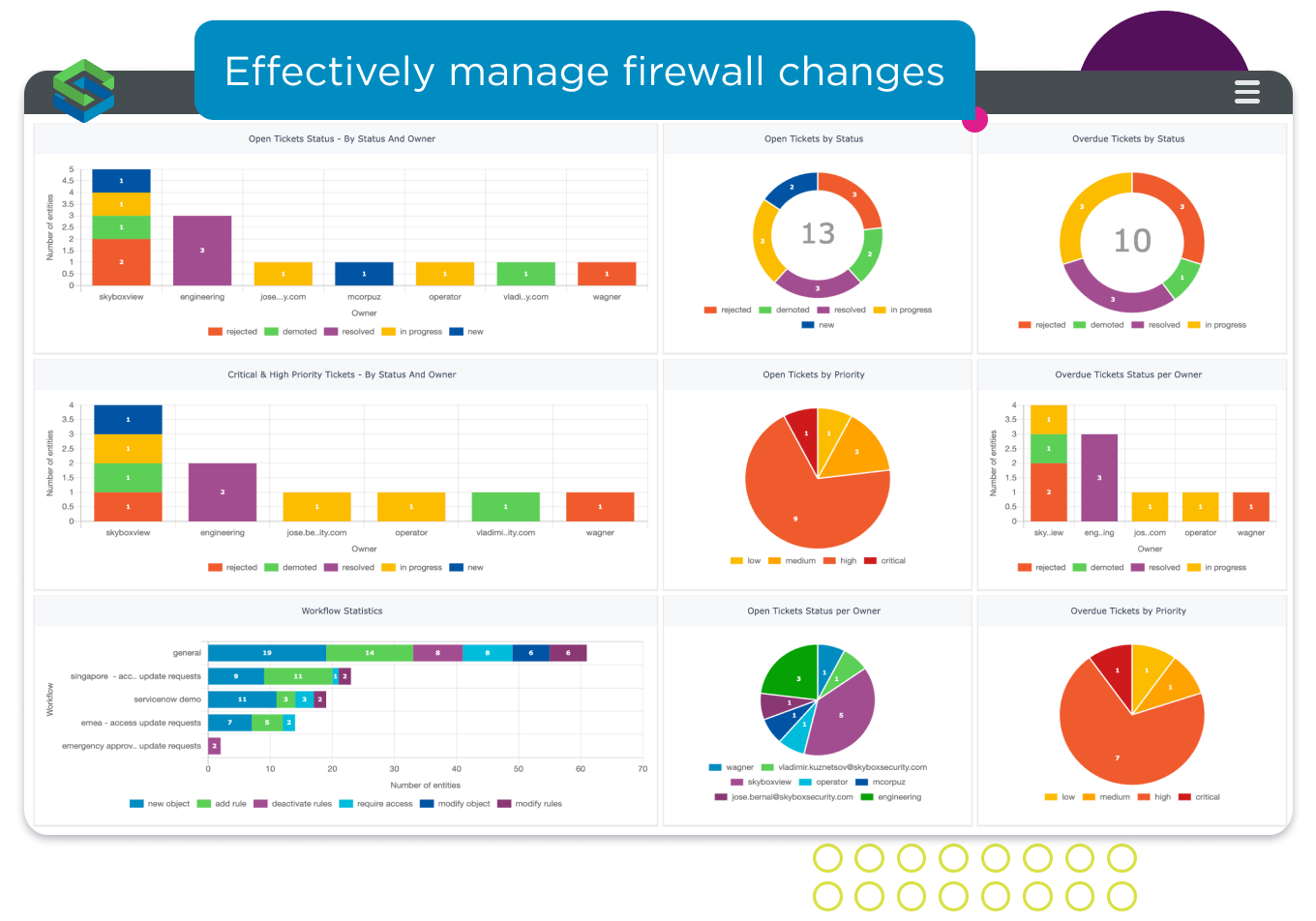
NSPM automated workflow process: create a rule; specify the requirements; define the workflow (fully automated, semi-automated with human approval, or manual) for a nearly zero-touch process.
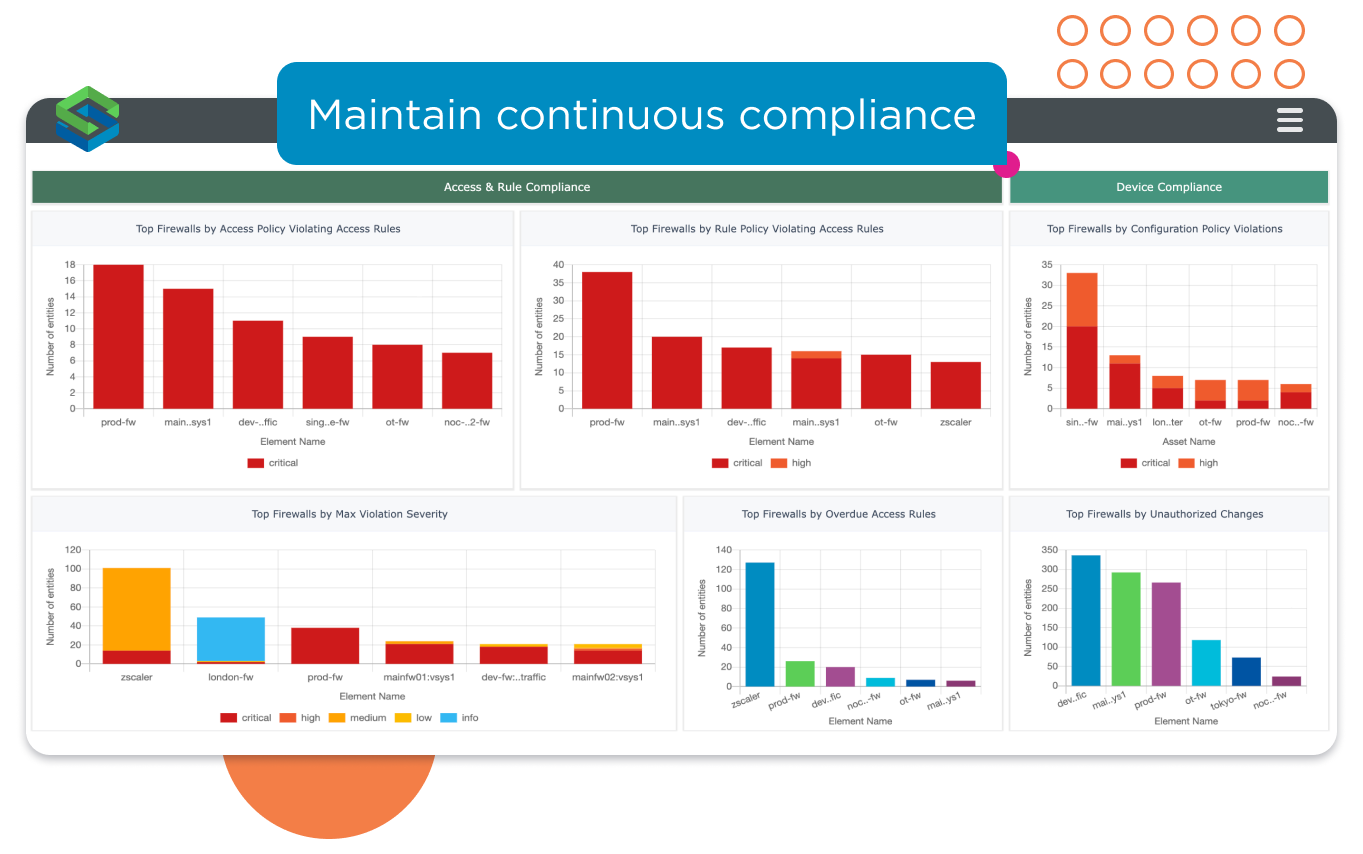
Continuously review and monitor your network for compliance violations.

Reduce audit prep time with continuous compliance
Preparing for an audit is a complex and time-consuming process, taking several months – or more – to complete. Many organizations face dozens of audits a year. Additionally, regulatory processes are constantly evolving, making it a nearly impossible task to keep track. An NSPM solution helps manage this process, making audit prep a quicker, and much less stressful, process.
With an NSPM solution, processes are in place to help maintain continuous compliance and help you be audit-ready. This is achieved through:
- Continuous validation of device configurations from a central location
- Scheduled audits and compliance reporting, customized to your requirements
- Continual reviews of configurations for vulnerabilities and policy violations, all managed by a single platform
- Out-of-the-box assessments for regulatory standards, such as PCI-DSS, NERC, NIST and STIG
Related Skybox Products
The Skybox NSPM solution includes the product modules that help you simplify firewall management, visualize your environment with a
dynamic network map, automate change requests, and maintain continuous compliance.

An NSPM solution collects and aggregates data from different devices in your network.

Build a detailed map of your network, combining asset information with network topology, infrastructure data, security, and threat intelligence.

Quickly identify unnecessary firewall rules to clean and optimize your network.

Provision firewall rule changes all from a single platform

NSPM automated workflow process: create a rule; specify the requirements; define the workflow (fully automated, semi-automated with human approval, or manual) for a nearly zero-touch process.

Continuously review and monitor your network for compliance violations.